In our digital age, sharing valuable or sensitive information securely is paramount, but unfortunately it’s also tricky. Portable Document Format (PDF) files are widely used for their versatility and ease of sharing/viewing. PDF is an open file specification, meaning not only can anyone build a PDF, but anyone can build a PDF builder/reader application. There are good and not-so-good PDF files just like there are good and not-so-good PDF applications.
If you open a PDF file with a text editor application, you can see what a PDF is made of: a bunch of numbers, letters, and strange characters. One can view the PDF “guts” and edit them, assuming they understand the structure, based on PDF specification. PDF Ink attempts to understand your PDF using PDF specification as a guide, and can then add encryption and passwords/protection to that PDF.
PDF security measures can be added in the form of passwords and file permissions, limiting printing, copying and modification and more, but due to the open specification of the PDF file format, these protections are not necessarily secure. Understanding that most humans are not out to cheat and steal, we know that applying security measures definitely helps us in doing our best to secure our intellectual property and sensitive material.
In this blog post, we will explore how to set PDF file permissions using PDF Ink, explaining PDF file encryption, the distinction between PDF owner and user passwords, limitations of these security measures, and yet how to take advantage of PDF security.
Setting PDF File Permissions with PDF Ink
PDF Ink gives you the choice which PDF writing library to use: TCPDF, FPDF, or SetaPDF-Stamper. All provide a straightforward way for us to edit PDFs programmatically, including the ability to set encryption and file permissions.
PDF Encryption is Required to Set Permissions
In order to set permissions, encryption must be set. If you do not turn on encryption in the PDF Ink settings, you will not see permission settings. Below in a GIF, you can see that “Document permissions” do not show unless the “Encryption level” is set.
OpenSSL is Required for Encryption
In order to set encryption, your server must support OpenSSL, and OpenSSL must be a version compatible with the server’s PHP version. If you have managed hosting, this will have been arranged for you in most cases. If you encounter errors when attempting to encrypt your PDF files with PDF Ink, verbose error messages may tell you that your server does not support OpenSSL yet, or that the PHP version is incompatible. Your host should be able to sort that out for you.
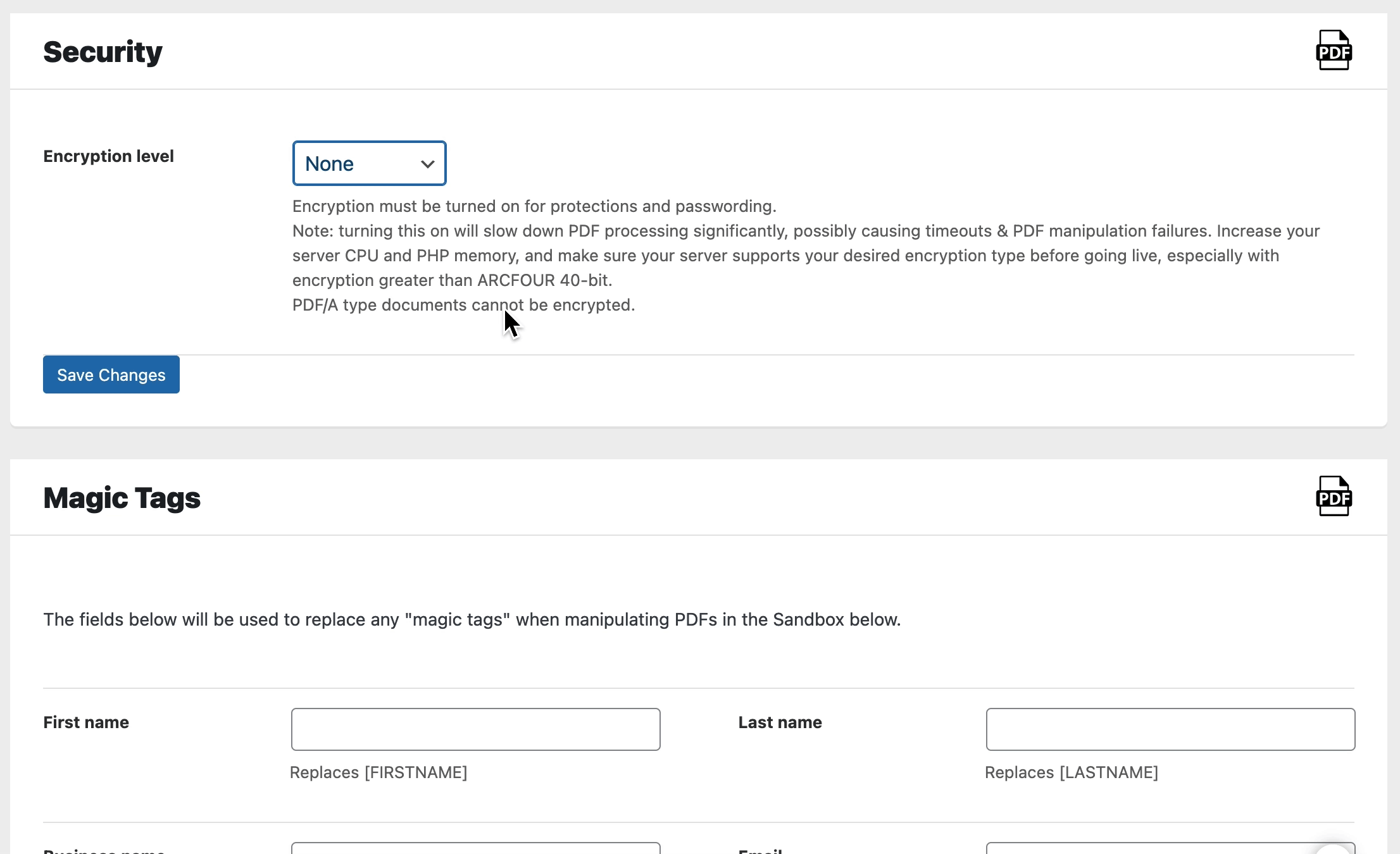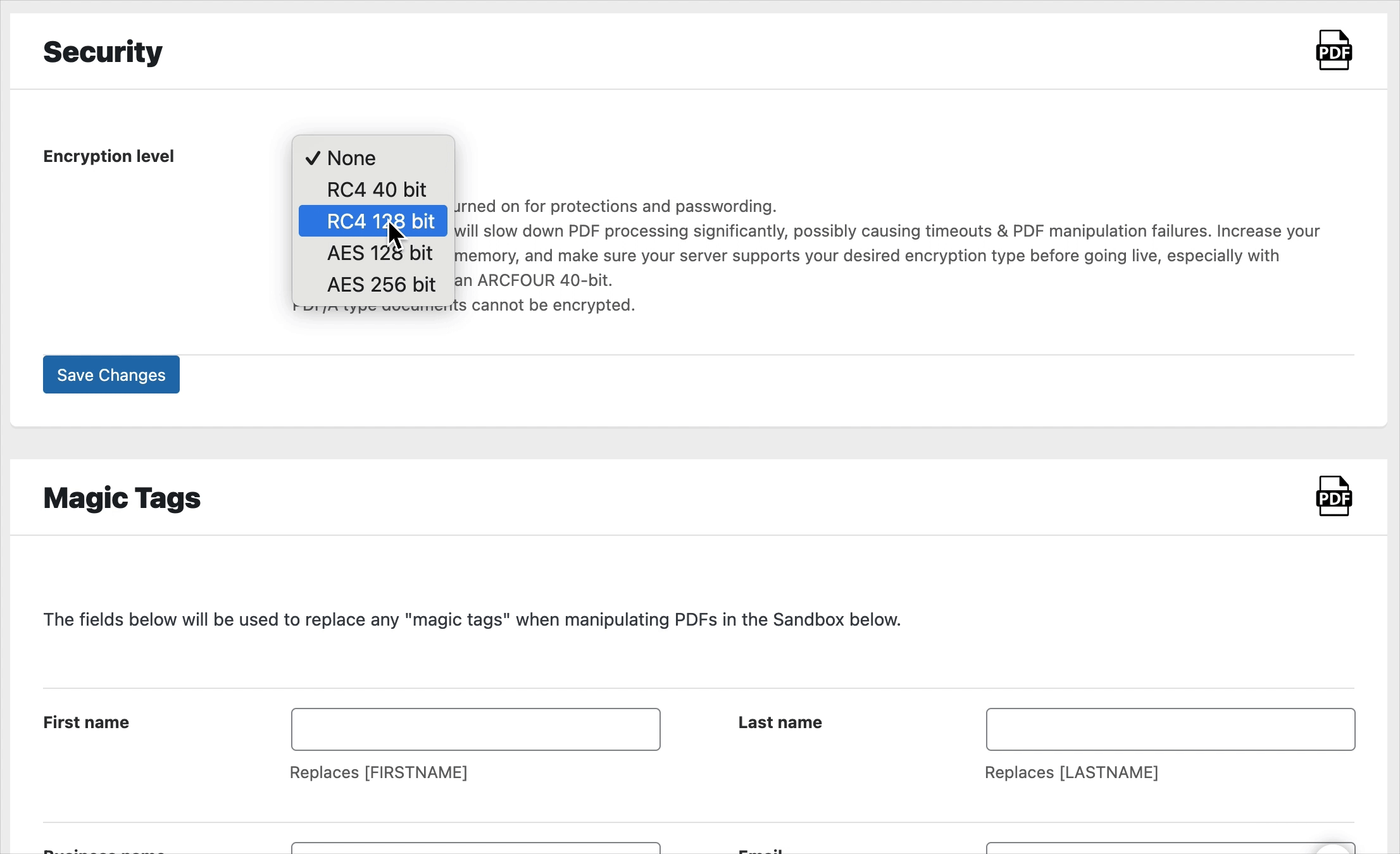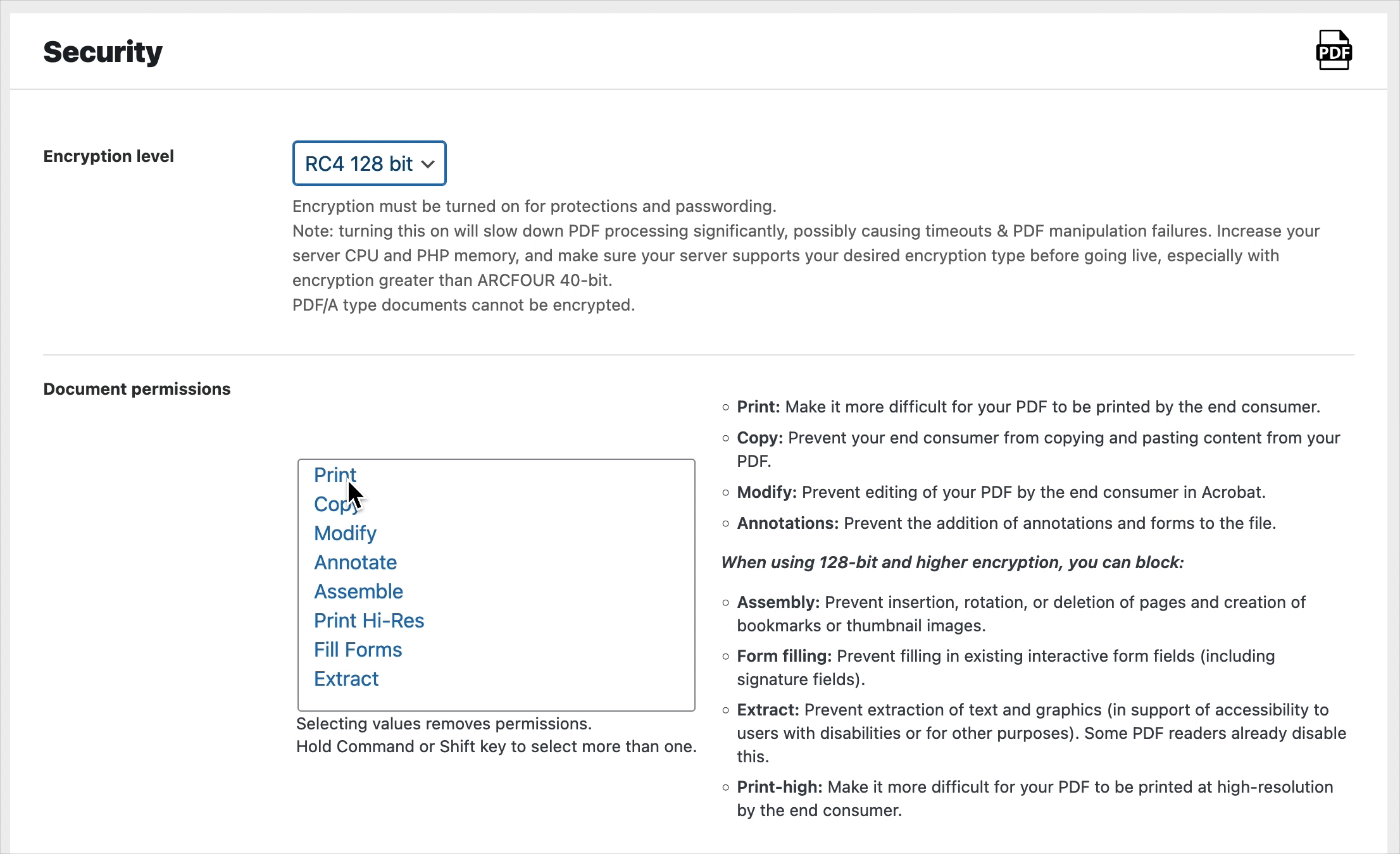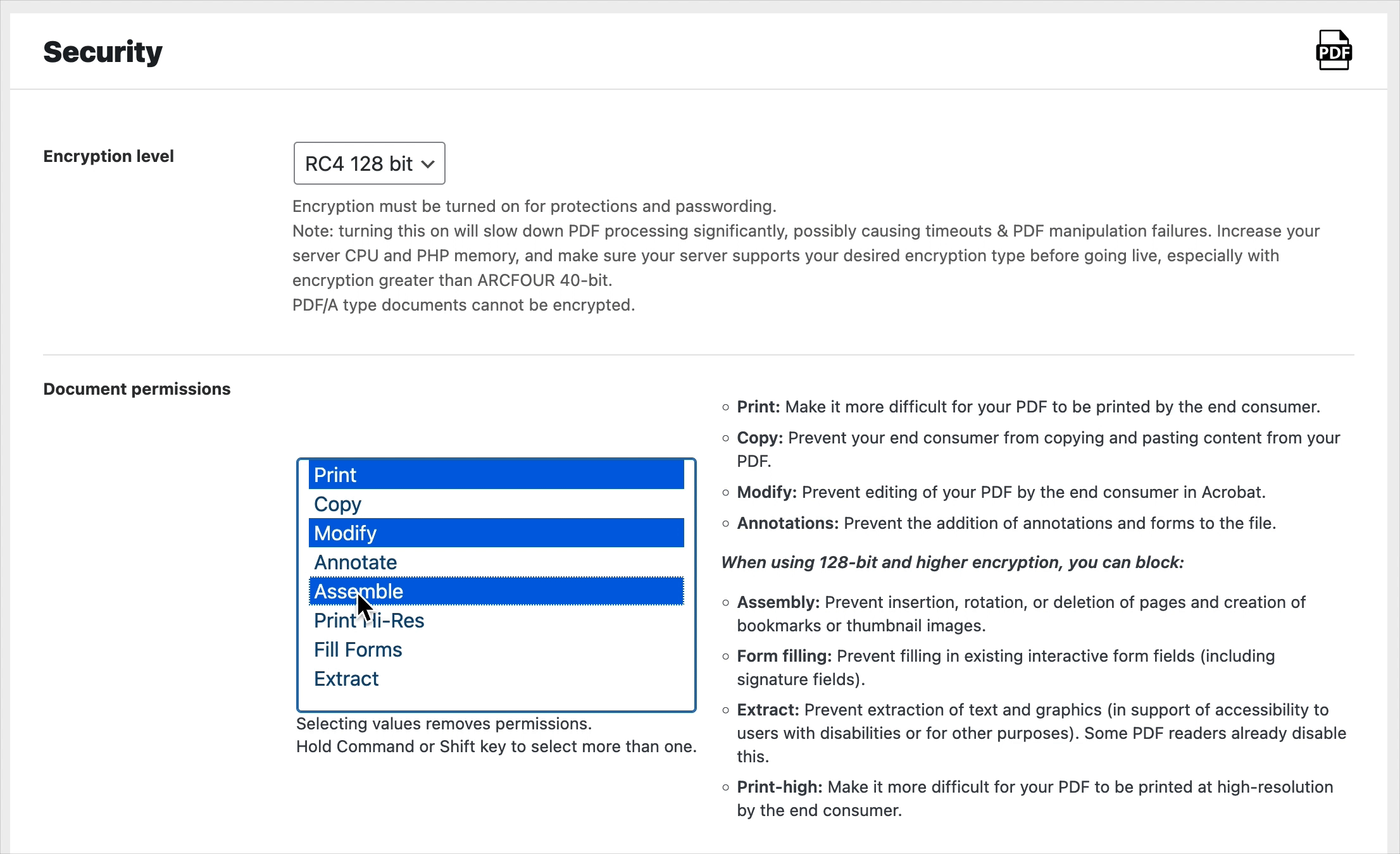
PDF Permissions
There are eight permissions which can be removed from a PDF if encryption is set:
| ⃡ | Print (High Resolution) | |
| Copy | ⃡ | Extract/Accessibility |
| Modify | ⃡ | Assemble |
| Annotate forms | ⃡ | Fill Forms |
Learn more about each of the eight PDF permissions.
The permissions which can be reliably removed with 40-bit encryption are in the first column above (print, copy, modify, annotate forms).
We say reliably, because if any of these are set, their higher-level counterpart is also set when using 40-bit encryption. So if low print is turned off, then high print is turned off. If copy is turned off, extract is turned off. There is no nuance. And remember, 40-bit encryption isn’t very secure. So unless your site is hosted on cheap shared hosting, it’s probably worth it to upgrade to 128-bit in order to set nuanced permission controls.
If we use higher encryption (128-bit or 256-bit) the permissions in the right hand column (high resolution print, extract, assemble, and fill forms) can also be removed, and distinctly from the lower permissions:
Here are a couple of interesting examples that arise when using 128-bit and higher encryption. If print-high is disabled using 128-bit encryption but print is still allowed, then the end user might only be able to print a low-fidelity copy. Another example: if fill forms is disabled but modify is allowed, and those are the only permissions set, then all modifications except filling forms, annotating forms, and PDF assembly (insert, rotate, or delete pages and create bookmarks or thumbnail images) will be allowed. Depending on the PDF application, this might leave no modification privileges at all.
Owner vs. User Passwords
When dealing with PDF permissions, it’s crucial to understand the difference between owner and user passwords. Every PDF has two passwords:
- User Password: Optional. If set, this password is required to open the PDF file. If a user does not have this password and it is set, they cannot open the document to view the content. A user password can help limit the PDF access to specific individuals.
- Owner Password: The owner password controls the permissions of the PDF file, and is always set. The owner password is not required to open a PDF, but can be used to open a passworded PDF if the user password is not known, or instead of the user password. If a user has the owner password, they can not only open the PDF, but they can change the permissions of the PDF file and are not restricted from performing actions like printing or copying or editing, regardless of the original restrictions set by the document owner. Someone with the owner password essentially becomes the “owner” or “controller” of the PDF.
For example, let’s set the user password to ‘user_password’, and the owner password to ‘owner_password’ and restrict print and copy. Now anyone who wants to open the PDF will need the user password, “user_password”; but they can still be restricted from printing or copying the content unless they have the owner password, “owner_password”.
Understanding File Encryption
In order to set permissions and/or password a PDF, you must encrypt it. Encryption is a process that transforms the original data into a format that is unreadable without the appropriate decryption key. In the context of PDFs, this means that the file probably cannot be opened and/or manipulated without the correct passwords.
Encryption does not always mean that a password is required to open the document. You can encrypt a PDF to restrict certain actions (like printing or copying) without requiring a password to view the content. This is particularly useful for documents that you want to share widely but still want to control how they can be used.
Several levels of encryption are available with PDF Ink, each progressively stronger, yet each using more server memory to function. RC4-40 is included, yet we do not recommend you use it for critical documents, because it is vulnerable to brute-force attacks. If you choose to encrypt, please use at least 128-bit encryption, or whatever works best on your server. If your server can handle the load, go ahead and use 256-bit encryption, but really, for most cases 256-bit will be overkill.
The Limitations of PDF Security
While setting permissions, passwording and encrypting PDFs can provide a layer of security, it is not foolproof. There are several reasons why relying solely on PDF permissions can be problematic:
- Technical Expertise: A determined user with technical knowledge can often find ways to bypass PDF restrictions. There are various “hacker tools” available that can remove passwords and permissions from PDF files, allowing users to print or copy content even if those actions are restricted.
- Screen Capture: Even if printing is disabled, users can still take screenshots of the PDF content. This means that sensitive information can still be captured and shared, regardless of the permissions set on the document.
- PDF Readers: Different PDF readers may handle permissions differently. Some readers may not enforce restrictions as intended, allowing users to perform actions that should be restricted. In fact, this is a common complaint for PDF owners who forget that not everyone is using well-behaved PDF readers like Safari and Adobe Acrobat.
- User Behavior: Ultimately, the security of a PDF file also depends on the behavior of the users. If a user is determined to share the content, they may find ways to do so, regardless of the restrictions in place.
- Processing Time and Performance: Protecting a document requires encryption, which can significantly increase processing time, especially for larger files that contain images or fonts. This added processing can lead to PHP timeouts in some cases, particularly on shared hosting environments or servers with limited resources. It’s essential to consider the performance implications when generating encrypted PDFs, as this can affect user experience and system reliability.
Best Practices for PDF Security
Given the limitations of PDF security, it’s essential to adopt best practices when sharing sensitive information:
- Combine Security Measures: Use a combination of PDF permissions, encryption, and other security measures (such as watermarking) to protect your documents. Hot tip: invisible (fully transparent) watermarks are easy to apply with PDF Ink and are great for catching bad actors. Even better: tiny and transparent text marks with user data interspersed on certain pages.
- Educate Users: If you are sharing sensitive information, educate users about the importance of keeping the content confidential and the potential risks of sharing it.
- Regularly Update Security Protocols: As technology evolves, so do the methods for bypassing security measures. Regularly review and update your security protocols for file storage and dissemination to stay ahead of potential threats.
- Occasionally: Move the location of stored files and change passwords.
- Consider Alternative Formats: We have all heard news of some monied, high level government or corporation being hacked and know that… ultimately there is no such thing as a “secure file.” For highly sensitive information, consider using alternative formats or methods for sharing that provide stronger security measures. One suggestion is simply not sharing the information, since there is ultimately no such thing as “security” in this day and age.
PDF Guts
We can’t mention PDF guts without showing some PDF guts! Here are the “guts” of one of the most famous PDFs in America, the 1040 (2024 U.S. Individual Income Tax Return):
%PDF-1.7
%‚„œ”
1971 0 obj
<</Linearized 1/L 149193/O 1976/E 32938/N 2/T 148631/H [ 510 326]>>
endobj
1993 0 obj
<</DecodeParms<</Columns 4/Predictor 12>>/Filter/FlateDecode/ID[<6ACA93FB2C38904C9CB3B4BAF70A2EE0><461CFB35ECE41C4191DAB8263D3BF8C7>]/Index[1971 46]/Info 1970 0 R/Length 103/Prev 148632/Root 1972 0 R/Size 2017/Type/XRef/W[1 2 1]>>stream
hfibbd``b`6å<@ÇÈ>àb…Åà* ¡˚H∞≠ÏÜ 3ê`Â- b3à`I ! ! $8AÍòwÇêsêh√¿ƒ»Ó
d100“Ö¯ˇÀı5@Äm‘
]
endstream
endobj
startxref
0
%%EOF
2016 0 obj
<</C 338/Filter/FlateDecode/I 360/Length 231/S 55/V 316>>stream
hfib```".V˘l~‡ ∞!G√Œ{
|flstptÄ8@¿¬¿0Ô<ê‚v∞»L^.É√\|b:6óY≥î¸:a‚Vt◊ÌÊé,AÜuÕè2&7ºRPgº†‚¿º¡ìa{¬$FæÉ*L
≤M
¨
÷,∏ 8Dfi9h0fiPi†@YÉ=ÀíLk¯ ¯@Â@ÛœÜ%Ï
ìô »3¸`ö «‰√Äî30r‘i
Ü˝˚‡¢Õ
å'¨Ä¥0C∆s∏Ë
&' ÕDV≠>P–
endstream
endobj
1972 0 obj
<</AcroForm 1994 0 R/Extensions<</ADBE<</BaseVersion/1.7/ExtensionLevel 11>>>>/Lang 1969 0 R/MarkInfo<</Marked true>>/Metadata 150 0 R/Names 1995 0 R/Pages 1968 0 R/StructTreeRoot 159 0 R/Type/Catalog/ViewerPreferences<</DisplayDocTitle 2000 0 R>>>>
endobj
1973 0 obj
<</Filter[/FlateDecode]/Length 405>>stream
Hâ‘S]O¬0}Ü_q›ãd_TîILîØË”“–ª—X ≤v†˛ª]∞È@
O.K”¶Áû{œ=∑ÃÉí˙
p‚ï><‚2!·
©
µXë†Ë1Å‘Ç≈R∏)ÜíMD
*u
7pÓ\⁄≈yòŒDÇ¿ô2úaÿ”\&∏ÉÑbhŸ1ƒ‡hΩq{Ô¨.›·∫u˘éNj†¬Ì∫˘ë`∞)· 9≥∑®T@*Üp
U&ßT!æ€B§zôπ ü˚$˝2TÙo¥WÏ
ù˛‘àI«G’Ô<ÊhH3iúÇ¡tfl∫≠fª
·ÌÎ
ÈÆN¨ë¬.∑[‘4y‚¶7˚ƒπ˝ÄÖ·në1•∂õfiM∆¡D†P•˘0∂≥j=Û»g¬*√∞E∆˙¸⁄¨«Õ^µÙ XÀç2S™Y‚JsΩOJ=Œ˚ãå˜IÒ!J]∏D]˜KÑRihmOõS-©Å
â∏ Ü
fÒ∞««‹ÑÊ&nR°›√#á˙wa{á:f„$√—f¨ˇ§Ÿ∏ˆ?'u˝s∆1˚ìë^øπ®ê©
endstream
endobj
1974 0 obj
<</Filter[/FlateDecode]/Length 274>>stream
Hâ‹íQK√0Öfl˚+.y+B‚´÷"ì)Ra”ÇOÂÆπ≠¡¨ m∫!Œˇn[‹d]
{ˆ1˜|9‹sï¡‘}Z2Ÿt6øªÁ
BIe£Æ)ôU $}C`u!)SIÊ{0¬BÍäOı|cE€s}OŸqflfl
""ôƒTV }cÿÌ`åÖ∏‚ó昒uÖ-
ÁéhªÁí◊≈S√≤wÁϵiÆ8J≥"ûöµ®,•
µ¿¥4+t¢∂
±?◊€Ú1zxn
nm»‡–Zn5∫ÃîÎÊ»&õ√x”U¥flØ’ÙA”X‰5Ê‘ç”fiïó¶ªN(;a,r‡}è=·YU∞ßUAΩ™èæ¬?®z r[ıèó$
â
endstream
endobj
1975 0 obj
<</Filter[/FlateDecode]/Length 468>>stream
Hâƒî¡n€0
ÜÔ}
"߸CY”≈∫§ËöÓh»ùpïEObb¯ÌGŸ›ÇÓÄ`áÜaH?©è?iQSȉj*{äŸrı˘fãLfibE
Ìdvva
[ÿ?∞îÈÏ”UZÃ
ñΪÌÚ.ÌNn÷€…€Ú
aã!è»ÔÚgáI±¥\ ,À¿ÖX]èÀ∑ç5Ǣ
cy
∫˜Ç¡îBGÑ[uÑAˆ;≈{J±F¥˙jÛ
ëÿÁ_„.Âz÷j‡qu
)Q¿ü
¡§“0¿qPWpé:dW‚
5 ¬Ê
ÉÂ÷;6V]BpJÂî#@DÑé˙—E¡å≠…ì"·êç?Fûoú=£ˇ+¯Äú¡57]fl>ÿ>=ÄÒ£@^…{¨"p5˙
Í¿yflπ≥⁄ú
úMñ~'ŸÛAfiãÁΩ≠}æ⁄t`)6Œts(Tö<
¥
^° ‹`p]fl∏~ã@á5zâP”n/ΩVO=R§B;ØÁ‘#GÂkj¶∆@Õ!πì¬çÙ∞˙b¥g~7⁄‚諉ÇÊs
˛¡ƒˇÈ‡}•£ïf
ÉGÅíΩ◊˚!Qj)Êh»ïœ°LN' ’Ïñú;˝;i2…G—t#&'' 0â÷°˙
endstream
endobj
1976 0 obj
<</Annots 2001 0 R/Contents[1978 0 R 1979 0 R 1980 0 R 1981 0 R 1982 0 R 1983 0 R 1984 0 R 1985 0 R]/CropBox[0.0 0.0 612.0 792.0]/MediaBox[0.0 0.0 612.0 792.0]/Parent 1968 0 R/Resources<</Font<</T1_0 2003 0 R/T1_1 2005 0 R/T1_2 2007 0 R/T1_3 2009 0 R/T1_4 2011 0 R/T1_5 2013 0 R/T1_6 2015 0 R>>/ProcSet[/PDF/Text]>>/Rotate 0/StructParents 0/Tabs/S/Type/Page>>
endobj
1977 0 obj
<</Filter/FlateDecode/First 212/Length 3213/N 22/Type/ObjStm>>stream
hfi‘Z{o‹6ˇ˜
tˇ9(>DâdQ#锶I˚í&π†Pve{/˚pwÂ4ÈßÔÃp®•dÌÆ̪kcr˘Œê£ áC*ÔM&3Â}ëÂí2eñkÉõc1„2cKï¨êE¶%4,rÉáù)mrÃÂô≤ér–¬óîÊ∫§û%05‘ÿ€¿ƒeÖW‘Œg•¥T2≥πıòSôµJcNgŒy Âôœ-ˆU ©,
*, Î@èÔæG˚{‚§û~’ŒŒ·flEˆ@
ΩÑä„≈ºÅÑÍTQB’K˙Q7ìQıÏÏ¥?<XL«Pg©ÓmuÙ~¯„¸â„I=
ØfiÜÍflã_é˜flÌ]-ÎjˆaZ?P cÒfih1?ü\<PZ“œ¶û]M´Íµ¢Çq’T´∫YAŶǒ‚z9™OÎJÚ»b^èö…b
J
ïN£j ÌH®Ωœ≥´Y›Tª
øœ«ÁɃ€;_,g√—è´≈™a15⢲—#òãÔ´O’Èh9πj¬Íì¶P˛ºö’´w{ˇ‹?:x¸Ì∑∞"Ú◊Wırux˘Ò¥YNÊ <⁄r
hÛ™ZR◊i†◊
„˙WòΩ√ÀzÙÒ◊Z§S≈í~‚40©4€*ÛÅ fy]√≤—(YQHNßö”úS√i¡i…))úïπ„4+ç‰Tq™9Õ95úF~,G…˝ÚÇ”íSÀı,W…rï,W…|Jñ´åÌ
ßÃfl≤ûñı¥Ãœ2?À¸l
ü‘¨W
ÂcΩr÷+gΩtlœ˝5ÀØyû4œìb~ö˘iÊßôüf~ä˘)Êßòüb~äı≥1e=
ÎÈXO«z:÷”±ûéÁÕÒº9û7«¸
ÛÛÃœ3?œÌ<∑Û¨èd}$Î#Y …˙H÷G≤>íıë¨è‰˘ëq\ñ◊≥ºûÂ
flÂ{∞˝’®û7ô/¥8¨ÆNÍ…≈eìYeƒ·eµ`ÿ´´jTãÒb:≠ñ‚™Z÷Ûi}fiÑ‹õã—b6´ƒÂó´Àz.ÆÍÂd1´iµ∫‘ÀÖXÃk—¸æÕÂ≤Æ≈9@ì8ü|™≈jÚY¨ÍO–áFÛ 4
-¶ã9œ&!˜€uΩB‘˚‚@
ä#ÒX
ã'‚D<flã ƒ3Ò£x.^àüƒœ?—3Ò/ÒZºoE%>àë
Q\àK1ˇ ≈TÃ\,ƒï¯M,≈J4‚Z|ø㜂ã¯[4u–È√ıtZ7¢˛˜?Êc‘§ûa∞_á {®aééß’≈
ˆ"⁄üfl=T a
l
∞…¡¥æß „j6ô~Ÿk˜ÜÁıu˝Ï,É
‚A®üLkÿÈ|0$*B¿o^
æ}ı„7Ω~∏غ\Ù95¸¨õ—•xË\M©ËuXG#•x⁄T”…h~1≠3)NaÔxï9#Œæ\’‘BH[,≈/º¸Ö≤Ñ~∞©`ìùR<ûèc¿pÒz2flüØ&ÌÔ„…r’†%¡–›¡¬&è∫>´∏â.
qz˝°A…P<µèõKÿ'—U¯IPh[¿Ñ 駖AdãïH9Ï%w»(îãùvÒB
ë∞‹afi@9 è¥≥Ä%¯4àº∆≈2
øÑ,≈©†5µ-C_J°?Ê© ‘!JaJ¸!%=@fLÀ8–∂Ä›ë%M¡3#^$; ÄÌ@L]¡zc=∂¢π~9 3’Afi 2Ê
0ç
˝1ç„«∂87ò«Ö†h':(Öò∞
ÍB”îÆ#vßµ‰rbÖ,ºÁÜ¿¡y’ D\yùo¨ÍÃ)ÆSéîAv¥«ºM\œtN°_¥˙M}
ıw∞ãF¢v¨]üp˝‚Z¶m2⁄L¥á>°
î«˙Ñ‚§+Æ˚9+À£=¥v¡vBièh^b}JXÓ…fÇO˜-ªcfljw ‹wR¯ŒÂ0|Tñ{2pflflŸ¡Ùcv8Ô°∏Ô¢¯ìÁ'˚GØáz vQ¸p1 ◊ÛU=NÅ‹or‰v$7™ã‰ª$π'íõØ…K ¯¿¿≈+¿çD≤ñÅèή^Úáâe‡Sä‡≈}v∂◊•Ï9êãòÖ∆é
£…√Âÿ/˛F ÄÙz˝&˝M…¨Gëá<ˆ']@fLÀDö
n≥n[¨e/
QB¯Íu?$‹ËP∂ÿè‰4ÅÊÒt>‰:ëÉ«@ûLúRàŸ!F“ˆ÷ŒP¢Eú•¥<‡x…îÉ8òPã2≈!pNn¨Ç◊ê£é&Ã
⁄ÄcÊ»s(ÍRÇ%£yÁ˛N≠©Hˆ¨>Öı≥É6õRÿPı èrÕ ≠7Ì˙ı(⁄Cjõ¯t÷9!\
Nª@Ó79A8
RÙ∂√Ë
Áq¨ÀT>∞‹çfiùyq›L{
l∑BÒãÎ
n∏›ÄfizáÆÕ≠¡Ö∏'vó_
vÁpåGá
,
1`!x·ÉÇö*ëxó‘¡¿S¸P±√mà⁄´¿#y‘N
=)£à»;Úy¬·wÙà—{¬r„S[<sL[œJi˙Ë·h†
AÎ@¿ÉßM«⁄5h⁄µÁO©@ۉ̟‡·ì
N ñ„X—3DØ¡ÁѺ+¯0 úpÛP·A„k…‡
<1úõ∏ò_É∑≥DΩπÀÉøl»ù
?MS≤é¥4õ–õºpÜØÈdS∂F–Æ|Ò¥f¿Z≠¡Ù‡
l ÇwÓãPÛ`x”ß x#¿„
q
˚
ºlN,tÇ O†∫·ùGõåÌÜφG(Ây”äD6Å∂¡Î>D4O…I+RˇÄv∞∂á
°≠s}ápÓqlª‡]‰õ¿?7\oΩ≈ı∆„õT»Ú6Æwµ’
¸Ó
†Ω…ƒ‹<ÒwpπÔ
⁄ÓÎÌ‹'ëæ_G
ΩK¨DjèÃπ †ç)Ü&∏”.¢År”ı∏·É¿üé≥¯—!H„Ü·ì<xÃñ√
•bêf0¶∂¯¡"ÿÛá:Ù°£w¸Ë±
@¶ÿ§esH√+îÊ!4Ä)Å=œÅ≥
`€E !Ô’ÜπâGr:z'^
÷ÖP√z|îó‰a.q!¬ÆI XP©¯¥Q*ÁƆRÎÑ2~≈˝°
⁄»BÚÑ#
aΩ»≠†øh(lîÅPª¥≠À›¢6∆SxA
M*Nå€PÏ≈ò Ã˙_‹êáHItΩc|$!⁄ä∆B∆–#äüxÊì̯hlqÒ»óº3Á≤C—(Z„à∆–kGƒ±»˛Ó„Fêvë;7 róÆÏ«O8úˇ¥çÆW
Uü¥±Ù%G—?ß_
;ËfiS
~˘Ô`¸”≥√ÏxYÕ?N'ÛÏ…¢πúåÿI_ÙÅ^wÅ˛á«á/N^|
bˇ–
Qˆ®ûMv`}π)ºb‹v¨óÆãı;Â∏ ‹+˘ı¡=ùÛ÷(l ÅπŒäuXÜn^.ª±í]îÀõ}
#9Pé‡∂&º÷+í≤úA§‰∏ÄsI{ù‰e“Ú>ÚñÃáıài¡yÏ”'
Øi1flû„9uz†ΩÈÚ√ ¥5κ—<ó≤;üȸî
ºhü
Œïd-»Ÿ.◊ıgóFri«~܉Áû(Sôÿ¿Fôt–%Ob)1Nc“¯JπnìŒcn∫u>!ZØ
‰eb Â≤K©Ì‹ π•úmgh˝…6ıp˘ç¯éŸL•
.7k;È ãÌÅÚøËf˜Ê5n∏æM/ow]›nΩ∏
∏®u[.j—_±t™ª„E≠ÌÓ@Øflúúû˝<
õπgxHô;^”nï·û;œWzGÀWo›;ZåYóDál{ÁF3fi—Zıøπ£›
QÑ›—°p‚&
ùËêΩ
j(ÔGá¨i7!‡íËÿ?Fv|fiÒG€ËP°{—!€âiù'„Û¸A⁄fi—¬BtÔhÒZVK⁄—A#DáxöêwèÎHk)Ur–(¯¬C·ÚöZ≈wÏ}Ûí6oe†ÉÜ17x√ ˜
p5ëhRqÇÙ˙¢üͯ†Ç/ 1ƒFa∂m·!ß6ÑáämÒâ5∂âF
c[xH⁄¡Ú~l? ‡a%fi¶fl:<dwÏ=É;
Ì'G∞O¸{C<v\¿nè
Î]‡À‡√
_>ÃQ Êÿ;‚Ω΂˝”g''«ßCX˚¥π„´úáJflÛ]ŒV!Ó ¯˜∏ EøiËQΩe˘+fl‰p‡Áˆor8≈$J∑Ω…Ifir
æ…Q˛VorËèfi‰Ë¡79Ìp¬Ú(W{∏È*˜VorŒˇ&'\C˙c|ïKÛr€79Jm}ìc<Cor®Œlxì°∑Gw~ì”ãY^ÁhGù79
DL˜„>˝?fl‰–ïç'õ∏ˇSÄÿ†
endstream
endobj
1978 0 obj
<</Filter/FlateDecode/Length 1631>>stream
Hâ§W€n€F}êò«p÷{fl%hÏ¥u–4≠Â<qQ–“ a ë*IŸÒflwñ§Æº,„¬Ä-€À3√sfŒÃûˇîó…"ûïÊÕ˘«ã´K†ˆÌªÀ
òPbµîDVB~?9øvÀ∏L
‹E∂ÃÚd <ôAûL"FTÅúP A‚Ôö2‡ÇDëÖ‹Mì˜ ÒºåmÉ5Z·#—Ak=¯8fl>Œ-±†$(%â∆*î˝ìÔn&ÁYZ∫tˇ¨ÿΩ'¯/ˇ~7Ï ä)›,o^kè·ˇ§OŒ‚˚B-˛5y˘sñØ^›|k;≈ñ[l…jHŒ1E âKêÇ
ŒjY¡1*)Ïfifltº´:Œ˜˙¸ê†8
aÚØ◊ |ÚB˘8Fi¬ÃV’iˇ˝5óD!•À…tÚg üzcè«#Âs
É◊≈≤Ÿ"2L∂¢É7t‘ØÅ?xC≠aQ≈ßûT‘G_rŸOµ=§Z÷0^'œ!2D#∏"F◊‡ü…î¿U:O
í˘&^‚«Y∂rpákWnÚ˙CEá°öB—U$›íñ¯íıÅ.›:ŒÀï>[@˘c‰..6˘”-ÁÊ
ëÛ„_ªón
L]˛êÃ\†ÿæ9=ù{ï$™1Rı.ï;í…T®kI¡*˛<à≠O fl¡Ô¶§zM©ëÅÑ˘p¬Rb¬Ï(c∆âƒÆ
e,é2fi —Çò·µ‰ÃV)_]O·s·‡S∫¨∏øà ÕJxÃì“AñCQ∆ΕÉ$Eïíäu<s$$Ñ‹á˜_Ë
ıg¢2
Ƶw°Äı©Cjÿi£-j#€—„ÅΩ!
61”{˜Ê;Óo
Û£ÆÊuféò6~ã˘]KÔ≈â◊eí•˚#∂Â≠µJD´¶¥–Ó
˜„bgßUè<π8áqäÜRÈK7# ÿ⁄óg^¨
O·Ql◊ÍËùªO“4IÔCzEmΩ(⁄N2∆yX2NO%˚rJ¨Ge
y¸†rúÖïË1Ïy q
Té∑ßb£ú·[S†»ÿëx[y
⁄jP fiÓú∆
%™Ÿ¢’;-!<®Í·MPá
$Ö%QáÿX"§C∏ÉxOmùYrtÊñ!Í€M ıûxFmàwn©Mßu!:Q!‚≈I
·⁄j¡îá†~\X .0-Ô¶≥^»,H?28%ºYA¶ŒA·x\˙¡Pî˘fÊı)»0√Btçm£jÊ∑ZlÄJ≥Aöeœ‘l∆B#ÿæʺÈäN®`—
(:¸FUµò{í˛ 69,íº(!çqáä”9¨í˘ºö•Iô‡v`À¥ÿ‚¬ÔQ;¬ES
CòÌ!Äâ.∆9h«b◊/«Ä~–„fi"£–~›∫–†í
k¿•Ø°C~ã∑
≥-yg˜oπˆ›?Çi)˙∫¶ÔOô
’˜R∂ôÆ≠Èy<ák]ˆ‘∫_ÌUΩ⁄Ô fiõ√i›ŸÃx·f‹#ü ›¨Óp1 H`…„æxükÕE)Ó›
t
ìÈ˝éV
”i€t*éܸ0€√£"Ã˚^yF{õ:!‘s–Zq*ó”Qù’πúbAÂUœ,8∏‘
û∂¯^T‘â|ÀåñW7≈3º*dõ¬·¢ ãa#
.
’ûçzb«z†Íç∂˘
„ÅJıy†«;ΩªçËM•√
ô1
x®ÃXT∂€ëÁë˛ß¢aˇk±< ˇ4̈øgr¨√]†∫†Ò?‹˘ÖŸ›◊–ü
î~∑+°≈Z!fioéx
i[∫c≤Ϩπò™fl
eΩˆ
;“µ
káxró®∞a+‘·[ÜÓπeÙX°¬∂ߺíˇ◊Ã˚‹|ûª¢Ä€óÕÙÛ∆áª≤sÂÌ+hóOŸæ∆x˛ ü‹efl—5›~ßæ}Qm’Å∂’
VyPC∑Èë܈u/´=Úêd5¬
Îh\÷x7∂ÓèvÆ·A—åvG…+w<ÎßuI ÕB,ŸbŸWtu¡µxı„#9V=
7u,O.Ü
¯îÁ-·°aC√∞ª%ÓçÍ
Ï«xñ√:√í-…ÃùÓ"À]rün´˝
‚eë¡,[≠óÆt∑/p
àgÆÄ;∑Ã
É
∑ê⛓¨%5áLfl
Úp¨Éf≠àU≥ÌCMzí?g∑·Ad{—V7!}›
J7-„“
”l€ï§Ç>ö·?mCIy
endstream
endobj
1979 0 obj
<</Filter/FlateDecode/Length 1768>>stream
HâúW[o€6}7êˇ¿á=$@™êIâ]—°MZ¥ŸZÿ{ËÍa`,:÷&KÆ$'ıøflG ]Mµ1êƒ∂x»ÔúÛ]∏úºªøEìõ7y/’¢DØ^›‹fl~ºC!CØ_øΩÉÔ0ä—‰"√ã Ü©'9åxRJ¥XOÃÁÎâ‡ûˇ$ìÈ‰Û (?Ä÷Ò|è
ı(´¡aÙÇ2èc“@ºÕ“Rß5@q¥fløù¡#jS∆Yzz$8b^˘„Ñòà˚.Ä˝≥øÔ{6õ≠'ó}¸ÑY§ØfˇV∞Ôf}±Ñ\ÇÃ
p}Å∏dàRú
`Æ'ÀA:‰«>˜†òÑ‚»â\
K‹Â∏¬3g;ã’fW'ªí∫ÿEK†÷∑‘æœr
?¶@Ô6-Û
J’Z£ë?ÁÂê~G %Ë`¢&åç—CyûÚ–zæ-‡z‹)HèȘÄ
E∆Åâ>0ß9
‰G3Hnç√ÛSa3∏GÊMû=≈ÈBfl•*ıçU}˜ì˙ éæUÂ0
ÊÖc&;™Z[·1Uç`“W÷hG·q`t∞F˛ú¬˚Nâ f˝
èìf°Ïì9}[3]2ÃáÅ-zB‘RáÓî ∏''ò
’†ãPèÅìjxñçc¡…lp»õ˘áËl |HÈÔçGc0¬
I°e‰SÆã8¨¯xóËÖe˘V≠7
àrQû߶Y-∆Q#®·¨c%Å€VÍÂ܇7∏‚&∞™√8#-1∑+Ω¯≠tÆQºDªl{ç≤‹¸Õ≠aå4`ÆY4π,6Ÿ∂∞O-„$N —øYúñ…Ó=+8«/~{Aô°«
¡ÔrhπM#ŸÌÃb’~˙!˚é
tí=£Á8IPöïh±RÈ£n?hœV™ÔÊúπÆ`
“©Q
ãK√HØ≥µâ–ܸùï”°¸&#Úõ
‰wÕ⁄árŒâ©¶\J®Ñ‘ä˜%€:CÁ›–°˜è
]4CoØ
››Ωq¥/Œq+fiie¡c»=˚
ÛJVYÖë˛BÍâ ÔÔ+ÔN°Ômã3@ÙòMµD
-fh!‘¸0¨ÂPñ&;‘6kñjŒv:îv
«
†&Ú∞ÍüN±h”ßÎß√Î{Ï⁄°e¿Æf¿o¶ı√ñ4¨ü›âv∆flµÈÒ¸µp«/˙„oÆ?èg;Òx∂?lI´ÔUû«:j’L4ø‘O:5≈‘⁄∆ÿd•"3Y∂÷Û+']›°ÎÆ¿n™|‹O’iÌ0M~œÂ£Mì?p˚h—ùÌêC-û
ΩQ9å¶ñ™˚˜”˘ïÉø{ÕÖÙ»è$êflºf
¨?√
¡å8œå O4ËÉcdK¥2µoï%0Ú·ènFÇaFFy$ÏgcîG§õ ÜG1QÛ»Á≠J‚ÂŒ˙cõ?≈Oˆø™'Ã/?OÎ.ÈŸÔË€>Û$ÃmP•DiÍÙG;˚¿ƒï
\XÆ4◊ô“}çEÁˆ£T≠µë¬é ’∆
j,ù_TãA 3ü¿ô⁄ãUúDsJiQ¡A 0 ˚ÜO™ŒÒÌÏFÁ4N¢Tµ
=lK;!ŸÉDz£S3€æt8Ç—é#
µ‹g∂@“–Ù[B`íñÁ≠¡¸∫5æRD˛∆(™œ≤4¨&„=Ùqú• ™˚™≈X√>}O‘˙EΩÄQÃX√ù‚ku¯^åaã≥›ÇçÎ∞a
kq0SôkUV#rö•á{
7@√OE`åÖù_ˆ ÓS@¸ÈM=8¯¸bølôU∂3W òÒÕ‹º”*øƸjø2ì∑J£ΩG;FÑG‚ºÚ͸≤–‡ÿ¥(Û≠ΩAv°*KµX!s&Ω6õÇßs˝m
FÛ+ß+ªΩØCÜlÇm›•>Üwc|…±ÀóF‚Ù…ó∞át˙íó/˘1≈æv∂Ê6#pÌÆ»·0ÓMè…÷∆bÅ¥úú¡Îµ%wfl9ÆçœLRoÔœª¯1.Urr Ü…Õ∏‰MQË≤pHÕy£•ú‚ëæÁ∑∏a0≥èPDt…©¿:‰Ùˆ≥4JKœ¯Rdm`YyÈôÓPCéD€‹$/≈î]£(éLç~ ô£`™ÀıB«O&èlÆÊ˙Y—5R’ü,ü_†ç⁄≠yª…3(˝ÂŒd}°°·-t1ø˙’ºù_>^°ì‰∫ñ±A•Ö˛æX©ÙQHîA˛Êœ1‘á(ÜBQÿ¶‡M%§2∫
<©`¯JU∫à·„ÿ‘ǢÖ. ô”ˆ„Û´fl`≈¥U
<˜ÿ √N™ÕYËèõπl¯ßġÖT‡nπn_HqÊ≈¡ú0ËïfÛ˝ΩÚã.\—ãn˚Â0çé^¯Õ˪ká£g#¢ÁÁõÁ∏ÚÔŸôiK
≥YJDËÖ|3,°yÄÛª≈‰NGï©Ã7Ëzí_
endstream
endobj
1980 0 obj
<</Filter/FlateDecode/Length 1466>>stream
Hâ§ó]o€6ÜÔ˝+xô
√Ôè°(–¶
–aΩÿj``Plπ—fÀ©$£M˝)…±$Jî›˙¢1d
>|œ{?|∫C〪}^•yÖ^øæ˝t˜Ò=¢J£7ofiΩág¯d9VHhǵ1hπ[\}fiÔ“}û¢Uí£’6…vø\/ˇ]|pÒ>,∑oã*€$´”ò¶çIë˚_‘Pl≠uq·ÈbSá≠∑ÌzÇ2Z˚yt-¸¶YÎÒnÿ≥¶/Ò›«ÂÁ^tª§ˇ»wπ9¬†V`—°Ò˜˛Äí%hù>•˘Ghh6†¡
√z.
Õ;4k'hà4dòFãÄYâY AÅ ß˝°LœD°( ∏tªëBg––
·Â@Ã
v%∆øP[◊GM"´“]ˆ#-—>$e˙îIïB:’°»—æ@œ†úoië:`ád{SVIu|€,Õ#‡
ÈÏ˙+∞sπP$©êÍ√†’Œ'º[‹–àÄ?∑@‚èâù˙r
ç˛e≠ç!pΩ]o≥f∑oø§∑Ô∂Y挔≤<¶
àÕ¬∆r
t≥√áVB5¶ÓárédåË⁄Ix˝∏fååk∆®®•hlY´ f{(˛r∫xÿÉP
“Õ
˛˛-…IÒåÿ+ EbòÙ–c=ìÈ˙Lx˝&«dIƒkt_#o
'∑ ©Ÿ£åO¨0áêÀu[ü1•Ÿ°Ms’4ûπm◊™G÷è#¥3Ï⁄éÿuXi\˚˛u™4pÏÀÖfá.â<ìR◊¬G÷OPö··6‚·íö
óèeOgAåå91ó:©‡u#:z1Ù wbFFùÿbÈfl‡˛wVÃ4f¥Ó√Ô€∂[∆íf#IÉ%Û@“0s¯ÍâfÕY˜Êß⁄Û!gUSæø*ShïyYáUïÌÛÚ˛:Rôåt¸õ8Ãfl܉πRóëóù=¥â;‘îc⁄™cÉvÆZ\™›PL†VùπTè0o‹@4xtúä WÓô∆F4¡ç€ÑE
¶’º’?Q'ÔÁFaÀΫ}jΩÄñ`"igÖxMõ„ní|çVèÈÍøa“èi≥À÷=±˚BΩè_ßkhö
‘#Wv÷à«àÓû∑?ÓpêQì`§k°_
-‚EJ
DD·∏vµHI8†Òò<â»ônì'ù∏´¥≥ö†É{ísLa
•Y◊ªøˆÁyRúp£[e…f‘’°»™gˇúAÜ∆)Å˘sŒªá¥à
6
Û.ñéJˆ}%ï9∫ÄÊß8ä1ÉmÒqE∞Åfi≈«ÔØ˚Ù–üÈ6ÒU¯ò=µe˚∞˜kÜ \¬éX´Ωªƒ∞ ¨F◊†_É◊Õ–ßruUê+Ö+\î´éq‘zi zÖ
WêÂù∑§Í—M¬flQ∂A_·öîm2∏S¡®Ç¶{G 5
oѬåkw"º ù…˝
ÚØYQV(Ovµ
æ
làRÃÖn\q∞ïflìfÒT~6êüÉ≈¿÷1ºÌ˛MDaG◊°†fl6üŒ¢∞ ç®
JÊ(∞_
c£Éöb¬^"06:c
∆9Êf:¡º¿Ó
≥ÌU…w¥*“uV≈Xà1Vy#;üÖ
∞Ä`ÊßX®
߉ñÅ5ÿ’e‡wÓKgEU†ı‹yë
Øìı Gò7
™ù”˙v3ŸÀôôû<Oπ¶ŒPDkÏút(5-∏I›∏/s2Ác—Œß©œöx†<ö‰®ãå("ëGYt€^”FJÃ<E>÷ê⁄> bVèÁ„ΩËRztj∏4btщÅ≤uœÜÒyÆ!∫“í√‹ àò78ãÆdÉ´«'f¡b€Å¡¨5»À∂+FMÚ¬3›€ú‰Ã◊˛\Ä™0∏z†é4ùϺßrww#Ï
Ov⁄S˚G1œW%âe/i¿W€Ùg˚™
ª3¥æ⁄Oñ∑ Ä4_åøôm—ˇ
wDCá
endstream
endobj
1981 0 obj
<</Filter/FlateDecode/Length 1220>>stream
Hâ‰W€n€F}ÁWÏ£‘Ùfi/@¿q“÷Ú–F@ ö¢†% R!âÆD√…flwvIJ"ΩÀ]±/-
ÜyŸ≥3gÁúbÑ—6√Ëö–úÉ6ŸÁÏÁÏ„ß;ÓÎı≤ò◊ËÌ€õOw˜
Ω{˜˛<
æ!∫7Z£å ökƒ
Œ1¶Hr∏ $7∞—æÃñaŸ°`ãÚ"&Üø∂‡ò As∫M@äú¡?ëËUáz‰D“·QqÜóLà~
Ÿ‰<
“ƒ8ñÿüG¶èª*ì´(1íÙç
ñSÄ¢J√oÙ∞$Ì
ñwıÁjMó{“5“÷¡ƒtÖ
öî=ÉE0®z
zWè0®£
ö^tÜA…3•û!¢h¢(à|•GK•"±ËÌE\[v⁄µΩHäû¢∑xƒ> õxÙû⁄l<*Ë•§DîÈÛÿñêdèUj‹c_퉱 càç«N'ƒÑ<v2§∆1é5 {lÀÙe¶£©œc5n™8Êö˘<∂ø:Ï:⁄∂u¿≈‰te»cß öÚyl2É⁄Á±…
Fõ≤¡
è'¿ò_‡±Üå{Ï,“<÷ú:tˆÚ‚n#Ω8⁄º
˜ôwª[≤yqN
Œ9t>d'…¬ç
씟I>¨/‡¶áQ¡ÜJêî«ê£
fl_ãh”Hm
á:~◊"ÜÑߥÜIòxHx0
fi∂†âÑ3ÃÇ-h2dÃìaû∫V4‰)≈õñæV$u£…àë2¨<ZÙbÌî·X3lFío”§‰ I”ü¶û(!æ˛îJ+°æ˛îJ(â1#«z£Ë'ÙõMû¸é—¢gK–
|r¬{Èsàǃ≤˜L@I.‡Û0ä˜~ñ›‹Uª∫‹ù#ûåŸ·Ì bof‰
ÕñêÊv≤•Çd9g
Õ∂Ÿ’˝n^mKÙfˆgkÙc+á°
”πƒ
ƒm]Û˙æ⁄oø\
æºq`∂†–gãÏÍ◊käVÂæ×ÌÊP
üß’œ P±[
ÔlÃı/hΩDuÒu¯•8†óuΩZïõEnüYpC√:Ω-©qÔfl/—∑Í-÷
¥´Í!⁄cY£¬EÁ Ó;t(À·˝ıÓPÔüÁı∫⁄
Ú1^è“>;'Ì(÷∂ '%s;ŒYö…Ë!ùπÄ0
∑#+(>flæÂá‰∫]:´ÍbÉämı
ãñ˚j{væ.ÛáÍ+¨Å¿¿y Ì˘SòZ(G‘˜Ó“1˜qÊ1Ìçüÿ≈–#∏¶n$ºˇuH©cf‹$(}m∞ © ëØØOP÷Û]OŸq
≤÷MŸô¶Íägs´˝Å˘0‚.mEì(:ò[áùL`fÔ5ùÏ,y¯^q2e∞ìπPî)yy £™◊K¸úkø7wååm+Â<∑ ^ñÒá1—öQ—˛X= UµY†r˚¥©æÅ4_ä«Ú‡åm_>U˚∫\†j◊◊ÚˇAØ,4†w*Âó*îë†B°Ù)7S häBa‰ÈU
yàeœ¸Â…˙d<¿_'L),»e¬dûQ®3è8É>@W$SIäѱíÍ∆Á#ädzºçÆü†;∫k®¡ÕzW"Rx[®S$œÂøAU«KÙ∑£
ƒ
endstream
endobj
1982 0 obj
<</Filter/FlateDecode/Length 1083>>stream
Hâ‰ó]o€6ÜÔÏ?2Öfl"Å¢@õf¿.≤°òÅfiãé5ÿíß®Ì≤_øCY≤ïö"i]V
¸)ø‚yy
ÚÂE˙jÒGBRÅ0Z…≈˘ onØQr≥HÆfi6mπ ó-z˝˙͈˙Á˜à1çfiºy˜
~«®D…üà¿ 1<sES"‡úbL–rõÿÔ∑ ÖØ·Õ&˘-˘∞v®r<®>‰M©8 atI‡{≠«äÔ`®◊u’öj¨IMbGzµ ø
ê]¨’›A¡
T*
n°4Zlì
≤
‘œÈQ’>öáD`~(;£àêT√쨶Îe.
ÓLt∑9îú—nvÚSªÅ≈¯Á“Éû«ay¨¬>¿ãŒÍ¡_Çq
ˆRú“Ωª≈¡\áX6àŸô¬˚ô"©Í˚Ú÷Â2/
Ù%/?õÌÚß-¸ˇUu
^ÔͶ5™+ÙS›lÔ.
Ô^°èó¡;cPY=∂Õße[÷’›ˆ'd¬X*g#Úç‚*ÄQ–gÙ\ºÙ$^–∑Tê9|
√ó`t‹§ àõØæÓHæ
ıı*≈ò`åEôˉa»ÑàÇ
+X√TÁ±ÒP&§ó≤E˛W~ø1®0;SˆüÀº1ËfiTfUl´¶fivÑ! 9˘m *˜<—ÏÖx˙F,ä,¿"ñgr(‘$á–fl0ù√°é›ÁF=BL†xâ›
BÕë
J`êdù»y
J:¡`îÅ.AfPÚ©ñá
±Ú0(Öó¡õÌnS?ôÊr◊‘üÀvµº®wvÔrq®”á∫ÁPw≠¯‚hÕOJ?xTÛSfìa93cJfO߬Ÿ∏9»*dÄv¬7‘
`Üé◊Ø(¯22_åÅ.=f/cQÏ)>Dåz˜¢˜10œ‡“dÄ´fl„ˇ
ÿ˙o~Ù4|&ƒ√À˘±7ìSƒ[íf∆fi,ãçΩ£û$!îõ¯æÓX‚µü¯ìÖ3äzÖ›‘«ôË$aÏç¬
"Õ⁄√Ωb^Óm◊p§4yS¡n[VÀzkNOéás#$çÔ/Áæ÷ä{∞fiw˜Ã–´DT˵]:j≤
X∫1Ñ≠4A5uhTdFÍUéÉ√∞>ÃJΩJá‘8
A⡶٠®â¡_‡˙˛ ¯›Á-⁄ÂO»lL«ûáF ˛≠
Ÿ”7öNÃ:≥{Ã∫P3´fß≥nÌ∫ág&VÕC‡0H™Ã&÷—ƒí2dÄ8álÔ+èƒGOFP##£—ÆËø ^åë.Eıå ◊«Ω∏gh¸<ê‘/É}Mî¿æa«œÇΩïD_\° V≠≥écr
≥Csoó
k_˘%))”ì˛Ë
˱≥ZÑcÊØ~Xh«’«t «|≤˙~à®›
«"j%Âj»ãO/§
KÔB˙∂(∫À#"9j◊M˝Èaç»∫è.Ù]–?
d|
=
endstream
endobj
1983 0 obj
<</Filter/FlateDecode/Length 1130>>stream
HâºóOo€8≈Ô˙<¶+‰ØÄ¢@툖C—Ì÷˜ÖbÀ≠äÿi
y∑›OøCJr$õ4)mPq;~‰<Œõ }ïøZ~ÀX. %Àuvı“æ˚pG≤wÀÏ˙ffl‘õr’ê◊ØØ?‹ΩK’‰Õõ€∑¯:%5…~Üo§¯(
‰L*ß»jõŸÁ∑‡”¯ÀCˆ9˚‘
˚TMØ:§…A≤g=J
_(ä°‰-ÓıÓq◊Tª°h—ã2ª’Î%˚K¢Órì∑Ñ¡%L^‡ñqâÇ,∑Ÿ˚7R>£œöˆkˇ%ìT
´÷@À
‹‹æ 6¡r
òË¥í*ˆ©Bظ~n3Áπ¡˝∏ˇ¡öBÁ*zjLщX1nÇ49y.gîÌ!∆ª≥éŒÊà¢:W„Íù´®Cä ∆%£"‰ZÅ
∏!
I§}X]ñ?ÊÄ∫ˇg‰≥^úZ€.BQΩ]»ÆY§H˜Ÿ™3[I+Ωà´M̱EøuTu+Ó∑—fi`√ >ˆ
CxL8mÆ›
öpEÄÀ\ ·Ú}”4ÂÍ+˘º˙öì[BlÿÌ…Á‡f_Ω¡ÿ˛8‘˚j
Égs¿ÿ•–ƒ¥|8(ŒflÒYÀ\€a*ù“pò qé¸â∞A'#∞P9ÿç„cúGP
k˜( 3:0rÆL«èe˘sQ˝¨∂flR„{˜’S„l.‹¯ˇ¸ù¿©„
¡4ˆÄ/“(÷NuÏ⁄9Ïcèµ\ôÁI¨˙‚¨Ì@Ç+:=ú¸„êZ∞Oïy<¥õ-8fô◊cŒ˝]fi;Ãπ±á80¯æ縆umøñ˜’s≥∫ˇ`4áflpô‚"rôö‹Ã‹√–Ó"5øôπJπHI„næèu3◊˛À‘Ñn6¡ã˜P}6@}™
@ˆ∑ºY›,hÏf&ÿ»bÀ<oãÀDû8—ë§SõJ…XẸÄiØ–¸>Ñà‡„”°|®7uµ&Î˙Ôz]Ì÷O/ä!#¯¯Où›3[ÑptFŒ ù–©ô Àú0~Çtu'ÊN!%sÌ6
\Iôìæk#$Ë”
iÆ^êdêÁ“«˝∫fiï˚_'¯MDí1"Õ á
Siv>d:îÜâBI†4- 2¶È AifC+oh¯†5ò˛‹f
Ñ÷_qa¯´cÑÆ.1Bq?#dOĘfi`8ûö}}hÍ«]„˙≈°BÅËÅÅ¡§&By—flèCtN"T4=1ÁÜ:œÉõ£]›âyP°<Ù¿8ù+IôPûL8h$ôË‘
ıxú'»‚)”êÑçÁCª1¶‹>
Pª
Ñ~)`§«EÛ?f≈Eã ?Ê«EÀdÄ
ÚÂáV~~LÀã÷~à ã6ÜÃnÔ"fifiܶAÑ“„GGyÜ%Qƒ@Ñ"Tª'èr∑∆Ô›°nÍ™ªk±ã,πp¯&‘˛
-Xa&∂æÒ¥~G
{%å~ı I¥ı{R
•åfi˘vv⁄öªfiÑ∫æß-úñL˛`@Òˇ¥
endstream
endobj
1984 0 obj
<</Filter/FlateDecode/Length 1207>>stream
Hâ‹óQè⁄8«fl#ı;Ã#ï®◊
€â-Uï∂ª}ËC NÀ„JUÄP“iIPؘÈo‚%'\µ:Uªa7‡
ûôˇofÃÅ√:Jêi˙g=DE >›Atsª≠ÚE:´‡Ì€õOw ÔAÔfiΩøßĆ’ú^%*@¡*
≥uƒù5o2em»†=7àØ7hyc–≠x?ânÓäMïmé◊àf
w_π˝ »!2ÓŒÄîÜëOú∂@O÷—h
zÚ5∫ôàœı'ãh4IˇNß´
“u±#„ı«Ü%Ù¸d
çX}+\@À≠ÛÂ√ƒÎ0
ú…è√®
2°AXsà"“[¡$[yûì⁄ÿ–4˚cÆ£.‘u$ıS$õ®ì∏òñxw=
yØfÎ J•Ê 9ù ¡,ÌmõEãno„é¯i.Y¢i;÷i}
äMŒcXoÏz]õ∫∂˝∫∂1ìƒñ†@#ÅW8n„{fNÛ•Q⁄∑¨•È§oä˜
~(fy∫Ç2õÌ∂yı
¶Ÿ&[‰UÈò°â´ÑØyóQr'|3NõªH¸îtOA"ÉNS
ı⁄ØÛ
–> ò≈Ê43)ÑpÆ}tÈ}Ú{ò˛5?’ßÖán
IPööõ!%˜ÿˇˇo…’‹ˆî‹ˇ"¡á…•LCJ¬_%/SäËn_)O:Õê*©Ö∂}˘G–gOÖï(tøµ zMbÜO·ùı‘>{jü`f/§è
¯UÏ [e¥À™Ä]ôAµÃ`µ[SÓ÷Oü‰≈÷Yµ,Êcò-≥Ÿ7Xf€
GeñAæ)´Ì„´ù[V>æ~¢¢./ tëúÈF≈ö°
ßlËß_3ÊD3fiߪ+ã∞'˘Ù¨¿ñNîp¸⁄dvOe¢‹ó¢†–
ë;ä¿`uUAÏÆj{®≈™Gyñ%Á∑#)댔Åà£
n4πs‘
ò◊
+sM•ƒÿO±ßd6SO¨⁄±2ÈAì¿8só~œ+ögæ§˘ä-q∫*J"ì¡mU•≥%<ƒÛ
ı©{»Ô ª|õÕP5ÿU˚∆„´‹_k4]X«*å4Z “á'ªqñ<Ñ≥~:j‹bº5Ÿç’ÇÎŒ1Z ¡¬£≥(≥I‹°<j§Úwjr~ ¬Rw"<‘qü’8‹Ye“flY5∂£ãÈQöà∑Ûy^wEb1flÃäuãm±>‡'∆∞ 7Ùó;∏ê˜û4˛¯€>’ù ]wO¯ÈCPÛ+:û:j—
ªN‹ûi/¶^ÇQ⇺‹0Ëù?
˝
ÓΩ »°íÅVz\œµQ•:⁄®7~a¶ï3≠:˙Ïs¶o∆e€É¥
ıVB⁄1[ǯg
8
ɧK—•ÈäÈJ∆ênÊ`Lñy ÙKˆ∂=*Ó”?™äÍPûù#%ˇ}]ˆe¯T&0äJ„f€
¡¥ù˝ë§
EΩÇ—·#lɧO3~ˇu«˘uÔˆ@"5ˆWπÃÁUnúZvVπ¶xHr∫ø»˘Ï8“Í¿ë÷RpÍ=†iÁê}OχT˚éµ»¨¿ñ”ت≤Z”Ce}ÆÌmø4™ªˆ+ˇÙˆ€'‡dXÉ≈¯Bܵ 5Wbƒ3Ò
ÈÆ⁄Q6Ü\¡g
ƒ"Ê~ò…˜Å «"–Ze‚å
"˛`z…
endstream
endobj
1985 0 obj
<</Filter/FlateDecode/Length 1546>>stream
Hâ‹WKo€8æ
ÿˇ¿√
R¿a¯_@Q M∫ÿ
∫h7>X(ñú®ï≠¨$∑M˝©á ¢
ˆ–]8±Mã
gæÔõ·Î◊ Æfi_#!zÛÊÌı
˛FxQ$Hà(◊òÖ≠6Å˝—æüSÜCcP‹üÇw `Õ≈eQ•ÎhU°◊ùAfit3fi.Éã´|[%€√9a;á∏-ã˚Ä¢⁄ç42ÎïòiÉñõ‡å“WÀœÕ¶}{¢µw±§Ÿ#,◊√Ü20∑åÉ≥õ›]UX7≥tõ J–∫»7ı¿`¥|HKO˘Æ@vkE‘VŒ¢¯Ûƨí›y ”∂´|ì¥ìö≠Œ‹*N∞lˆ√vL±¯Ü.fÔñfi\…}
“CÑöa
†!&ÑÓA¿‡g¯2Å’áî5 eêP1Å)?btk” A-fB≠±l40{≥ˆ@t‡oŒ≠¨9l¿ø" ÷ÉV‰0å‹@flé˘ƒÌop˙˝—sY觢ùa‹≥Yáì´^<%
ßÏ≤#éÓ≠2ç5bD¡ôı±Ynm∫/+
Ü◊vhê®?VÅÄΩÎÔY Êí6T˝{Ω≤
ÖvÖrî…Í/¨~^Ø»ôvºgAΩ£
Z=œ˙∂
‹AΩòQ‹Ø2 ç‚‘
6ƒöpóõ*⁄∆Q#Gg{XLârL∫N‚›™JÛ-ZÁ≈-cjDçTËQ#È“Mê˝tS≠∞ m
∫I∑˜YÇÚZÇENÄ®⁄ÉQQ§ CÎdÎ~Ôa˚ºL
£"™íÏiÅ˙O•·B2Êuß°Á›fi
¬lW;ˇN
{˘9O∑Uˆ‘ù‚Ÿß]î•Î'Xl ILi)∞4@∂0ƒ≤ââ[
b≈é6(w≈◊Ù´u†|Ãwe≤®mÌÉ´CÃa Â̓î¬
Í¡aLòY∞Òò»âò¸ûD1 ◊˛X<Xˇ
Ú,^xڡˬåÔ≠&ˆ~ø∂
≠
í’Hã◊Öh˚ÑÓÚÔh∑çì}iì5$è
Í∞flsµÉ˛i—´èe%hèl »icM‰À$ÅäYVEm°ú*HJ˜ÙXP†b3d
¨ÊI≤®lZÎ˙Öç
Ã&ÂXì~akÏ5˛çÿÛJî¶~âÚ‘∑∂'ΩbMuc#—ùƒ ıAmñ„°§ˆ˙üºòúíV…&˝ë
X-{knœ\Àupçw só∑Ø˛£MìÊM”)f5M:
lö´L–ótMZÃÓöº∞ÄÙ7MÕπg6MZ
ѱÌñN):´c“z‡:3+à>Éf˙:c»¨Îå]ˇ\å˘u
ù∏Õ‘Ö‘÷‚ª] wòÓZ≤'`}¡˘-/6H#l=ÓÁó5ÛjX˛ÃT3lº±nÒ
Ÿ
Ï´ŒñYh&:k?¬πúÛ„a ¬À98˘L∫ô°´^K7Ry
›åÁ™◊jÅ'~”t3z›Ã,∫i≤øÜ√tÉÆxÇnóqå2K3∏p!®ü–[:ôü≤r˝ˇÜ√¥êÑŒ•èK…
ëêÑMàÑÄâHÑ$|ÆD¯1<ã–+ÕŸÁ…Ñ$b<†çZ
*Ó
°êD≥÷1∏EL≈“gVM Ö$zñ\Hàxi1¶fB-nvwUaù¥íñ∫◊äÌ≠ÌGR‰∂ gP∏¨√’Ïúúc¥|H°íóˆZ◊5›mèç™Ë{tó%M•Ôı◊uI◊ˇ^I A%#
∞C‹À˙UIÈ\b@∂X/[fi2//§|F∑*)ü≈ãS°ô≈
érlr%üœ
*é∏·õq–» mÀÖ=å«
߉T6˝YT~¬)7RàK$$|õ?hK—uZÆ≤º‹…},“Ø—Í ]ƙִ∂ £«§¯ñ_–ü]w
— yïÆ`Aô$ˇx˚KTDïÂGYÕ-£)lË$ÛP`fiU
Û9!0= 7LïnâBÌÉ06
Ú`#qUNÖêúë∑Sæ≥!
™m—;ı]ËYŸc«
l˝
X¹˜
€Ãm–âN7
é≈∂≈‰`:\1âù›Y0v;òÇNëåÊ
_
òä)‹
V›æ:å˙GÄØl
0
endstream
endobj
1986 0 obj
<</Filter/FlateDecode/Length 4599/Subtype/Type1C>>stream
HâdT{TÁüaÿŸÂ·";5ª∏;Aà·ç"OïPAA@µ»≤;Ë cuy(≈ (âû$‰m£ûVmQ4`}Q$´∏†ku’≥‚£ñû;xÈigÈI{lˇ˘æ{øπø;ø{øfl˝H¬Ÿâ IíÀÕL\∂$- ô/ƉÀ
:ÌBæÇOÕŒ*◊eK¥•éç†"ÖIŒÇó;ã1∏ÊÕÂ7©xÓ!(<èz±r·$f"ÄtN4Æ≠2V≠.Á¶EGEäktËÿ»M
ùŒçmaÒzcœeUïïÛ%e‹¸Rù—¥÷h“ñÛ˙`.æ∏òÀt§(„2˘2fiTÈ8¸7ŒP∆iπlìVœóhMEú±P¸f–Û≈ºio‚Êò*tE%⁄2›jC)_ ≈'q¸]qEô°í/Æ‚ä
:æ¥å◊s´M∆äU´πTC©±ºj-/&≠©äK*)H‰¥•zÆD[≈â$M¸*ÉH”$Ç
•úé7ïk≈}MÖ…P¶7Ë
∆“≤‡êyYŸé$38=_Hàù BB2'bú¡Ñ˜;DAƒêD¬ªÑë bA§:ZñFdèI72ë‹D
[»ã‰}'?ßdßœ)I5Rˇtq˛N‚%âìîIzi7z›-uïKJõ•w§œd*Yö¨@vPv«%¿≈‡buùÌ⁄‚⁄ÌFª-q˚ÿÌàªè{µ˚Öq‹∏™qmÚ9/ˇD~F˛‹É»ÒhÙ0è
_?˛¥ß⁄3’sßÁû®ò©ÿÆ¯Ω¢C1®ûQ◊!
uê‚Í”A’9
µ#£µ4|äXåÖ}xJ#á?±‡pF˜JGȺ1bQÙi·
Î∞–·…Òä|£%£r§z˝¡ıäo≠
l Ì÷∆,Ö=B8õ¸ÕÚCΩ €gõØÌUw°çÌ´<øÓC%s,|Ò™∏Ìj<!Ï®æ ∑»¢ª•¿|˛§ X%x —딧Nfl/Å›“K[[tM)2+Ω§©7ëhí1_^œû/EÈ∂i—8Nâ.◊¥ûAç§Ã˛ôMã~™}$â +:ÜÄ"ÔE›^≤È_m……SÁJÔ
Ôπ´
)©
pnÂõı‰ápAÖ0f)!‚{≥Éø:ÖˆEØlúç°JLºåSû°ø˙ø8ꀮ.˜WÍÇŸ™ÑƒÖ0%`
g«†Ôq*ŒRbD!˙é·Æ‘˝¬h¬E∫°Ë£‹ºèd"£C«/ôïØ∆-É
ŸmT‘∞–f¡6˙-PÍ‚Ÿfi=ï#[◊ìUÇÑ™⁄»ˆ—„»VI-Ø6
=f≤ÕßlTºb1Ù+ÃòæÇ|Öiõ! Mh⁄å˘8Mm´gáÎ!|¡∑
ìΩfl€ç…Ëãæª!˘Ôj˘¡J°±áÑflZ)FrŸö€∂Œ_ï©£çV©ºŒ,ú7ìÌV8*6èÚXkm€„*ÛïúXøÖ+—=^35-"}3Œí :Û(A˝È©Gù≤á]˜ØÇß&˘›¬ÒË ¡°œ^µ»˜¿F≥‚w÷πVh≤•€ò◊P
ÿÜ˝ÍøV›øæbz¯úú(ˇúkOj54æ_kè º
‘œ‡m’ˆÑˇZ” eÜ:ømÔº¢Ñâ¡—ΩÉPµCm•Ô’∑ˆ>U›Í‘≈«¶Í´´ÎÍ∑hƒÚ ∆L¬
%DäÂ%—x{T+âÜkcÅògÊ)ˆNÄ≠R“Ä/
}ÖA3Ñò…?X·úç÷姱¯öû?Í‹∑S“z¸‘ëNï˝œ…A(ôó
ë—’∑√AÛùO_∆Åá
¢ÔÅ
‹!¬gÀólZ]¨Ÿ’–
˘hK‹kÜyfE≥⁄≠smÃ0¥ûÏ–ÈÑ∞»úÑê‡≈7 >:◊k◊0`*
“è∫—EÖyòÜK—ÔfC°FD%]’kòÛΩb”ç):Ò ˜¸fÄØäÆ∑kÏsî-¸√BÇ∑ù>K]9Sê—Ëá”Qä∆M∏MfßõD𻆠¶Ä∑lÏfÃ5ïôY—jK±¡N[öçÈá ∞Ç
ÏÓºoÈ^;+=#",ıúUÕ¥•¿ª†5„bôö9=Àòó©Dfl·9‡ˇv&?,∏qDÕúπp∏ı¬U•-˝1Üà$?XÄ.∆l´e{œ7˜‹Ë‡Á$ÊjìÁf}◊?¶åyé)Nÿ‚¨pÚ3, ≈ldV‚ÙËE∑˙ˇ“< ~6nÜö¬QÏdQ˛Öu!∏© Ógò
ª‡ RΩ8IlN¬…»Y¸¡Á∆’ÊK«4
ª$∏`GNË3îî’rcªÊflì¸fliJgQ¥Ä¢ˇ/Ê≠A>qi∑YÊò‰∑ "@h3+∫¨˝@˘[Ô9Æò™Ÿ'ªOıŸUΩßV&4j„WÚzΩå“ÈrÛ¢ï+¨-“ûˆñì?®€€⁄N*Å ÎÕÖ˚‡‰µàè
≠fy
.ãR.≤¿Éu΀Fò;€&<ß-P$Å.∫ ã$√4
…ìx”Ôép∂Å7| ¡
¥¸yùÍ,€*aüE—oª=≈Œ‹Öx∞∞PB[ÃÎÇg/Õç÷`
8ìÖÁ4xõ_kò3ówá
Pㄈc˜ë÷?›Vfi,<ª‚®˙p~T]™
ø§Ìbp&=xsÛf n•
5f“rPm¥V
y“.,∂S#ë¬N+–√Ç~*\ãÆ‚´C=% /Y¨çÄy4Å4∫÷$Ü°ß
?Lu ~∑ÄÉÿ9Ô£ëÉKùE8k!˚ÌǮ˲ ∞ãÜöaP¡'ˇ‚ªJÄ¢8≥∞#Œfl∏!√:Mèªå€£qDE@D
^@P.âW@Ñ`‘D7*1 ÉÑbH
≠’4xcm-"f%Y<‚
@–·hà£2äSh≤j|=yù›}=CjÀ⁄ä5]˜ºæÔ˚øw4‰°7
ƒlªÖ2àn4S◊⁄֗΂MÃt\Ù¡¢ÜS¨\$)£†DÊ$Öã¸Ç§ºœtÎI[ÈflqÄ]v—ÛflI
b53O Åz ™$=Q[m„΢|Á√EŸ
ØD@.„Η∞5ƒå£ç2âåÖ¿Vá»ün•·ÄJìÉAD6˛æ'1‡•ò<F¡äˆ#÷≥ƒ—Ë∆p—¢“ÙÍáA€KgF^Tº‡b˘≤koé3√¢Èvxt‘'L7;Orö,ö}XGÈ>«ô!(ïljvjh–ªfl|/~
ê…°Ø5í™hË©˚}¢NrÔ–œt3Öéa˛¢/ÜW‰È5
◊¢7√£¨9Äöĉ‘ı»´$EÁ‘—œ¬—`A9Ú
“Kvπ ŒÁJª|áú˜∂rG€E˘é∂Tπcwf†ÅÒuò£Ù·ªrüñVD∑å»r‰AÜn∑À¥ÛÈÌ;„flî[J9y∞“¢}‰Ãò»¯›J[1ßx…mZ?äãt˚´∆!opx‘ÄS¿d‡0,Ù·»Q…êåtE
}Ë>&ãòØ—YDA‘5ÙG3ö£ËÖQQt”,∫´NÇ
ı);\™‘¡jJÑM̸ÅöÿÙN|Aƒ+.á%±'ıã√¬““áb¬$7†Ã
ÁIÔǃ◊ÒπŒîb!–™mm©~
flˇ√CJÙCæzæ¢Í+ëœMàñÓÓÑ•Bg¢v˝™?-7ˆ√{˙§∑B,4¥iu˜ Ù J]†ˇ„ÄHY†
πûöWbFŒx'ÿÑ_*LJÄ
êœÓÓû≥›T
ì?˝≥’û?±◊Í∑t|ÿR‘í◊æÀ≥îªy†Êªõ濬ذØà=Tj\Îè⁄g;¿nßrqçoó;‰R&~à
ÕËgD
4D
n%∞µ&æá˛ÀÎk»ûÑFü/q"#ßQg2¿ÿÄ·»jë
˘v‰!€y€∑W:,›o
µCTs–©£ûUDdä»⁄:öëî¶ÿ‡.*™≈Ø;d **√\Og®èõÖ^®ènΩ(ß”-ÁÉ&
a÷Cƒä:∏[^cr‰>`d≤ø˛ÏÀ߸ÏßF3~'é"ó3
&óöÜ∫W√iÂœ ·ó
Ì∆øS»Ø‰Ë…J ≠U´®©GÖ/ÌÉ.√^\ ΩZ‘28¨º®≈:≤ßñ
µdÌì/{Ï3»ó%eì_ñOi%•2B‚îπ )≠.ïÊ8£U_mßqh£çÔï} VH_
ÉÉ^Y¥Á\„?˜ú€.ûfl~Èìø
?ÿTdÃ.˘¥÷ï
<Ô∑7»%Êò
Ù˘»dcm[ŒÏk5~›Pô±5pùâÔ
…
]ãÉ}ÕÌY˜Zû˝J\Pıˆâœ*À˛R!Í∂XȘaéE’Mvæ^~
v ~K«†'^|Ô_}'ÓÉÅ'˝E>_1„.¡FïÆπîK™i≥ú1BpxÉ ¯M=ܺ∑v˛S1Ï c˝ƒ4’4Bï¿#º
œ™„LxÍp<›¿Å
ÜN+Ë+M°lZa⁄¢)F
Í=«„ö>n©[ø”Ù¿j;4Q’ï˜ìÏaXYÃñÕÿìlƒ‡i‘1˝–ØıÚ›ïÉÁ´L•åœè±Q„RÃ∞M¯Òÿös8 ?s,ïfiÅ©˜®@òn?#ú$òS \àÕO[cDmädfllíá2R∂f`ÇG墻ґO :ê¡#xv
løIÒ≥–πıÃ’
„çܯ∑–pqÇfØ$+¨ XÙËL lr“÷—≠¨Ó¿Œ„üTAgvù„{Àfi{gÛ{∆†‘Ã…¶È°3oq∫ı∏º ÜYe°1±fl_H‘™6
8h≈£fi'z@Û§6pÇñôxlê
åÔ勃ùsfi·x#Œ~«ëƒ#⁄Òy∫‹t§ë‰X¡–33=Dfi∫ rfl∑’ôU[Éñˆar˚MòÍö”Tô5ól∞√Êq…`É:÷{≤˘·Â⁄%â">¥A/
;Y
8lN‘[s÷à≈pàNY—P\π¥è4Õ6èf"Z
∆lê*Ñ祩O1ÕÍÙ˘ı1…ÂBòrÖ%Æ[^PXRZ Fq WTl*7ZÎkÔöú{π¬fª˜\eÈflRòt
bpø(€≤°≤`Æ√B× aú
áöóÓgAÉJïí™#1*Pˇ|ÜÒı*/+;v¥˜«∂ΩãbEºKKN:s∫˚˚›) ÍRˆÊûÃ˙á9.i¬7ƒ∆úyç/Õ[5oô©òÒ]mú[®ãfi•fl˛
°"Á≠Jx]§∏∫nä[ˇkBÄ’ÓQ
;
w
üÉpøE˝w
Ñ“ºé·°¯
àvË[[zzZcPèC¢cÇÉ£[`e,ΩëB̧sßl◊oߨbV≤Ï)eœHW∆˜µêÑOÌÏŒµ.æOfiØûQüUÃ=#flpØç)f9Â7r
∑ëj vR≠¡∆77êdy
ÜûÏÄ?âvn¸Ê˘KñÑ{飆!°B›%Òà-“y∂X;ıûû#0Y@ü≤˚ȇi|
\-xˇ0π*¨“ƒ∑O≠ú∏Ω¡˜Ù7Âߌ]»â€Joņ/öPçÃ8—¸Í»1∂57r©7Ÿro∆˘∆G$«ƒ
h˚ò
§˜Z´¶èlÔ
•Ç2>dÊmÏf_w[ºl]J&›vÃ◊ ZÕ
Ωúd©ñÏ?Û:πPÎXPÍ,s¸k«ExÜΩ
z|1
Ü]ø˘•jëJPÓâÿî‹åw≈ñˇW?rÑ
~Tu}˙[Òè3®∂Q˝·Ã™√ˆ=‰œL÷g¿4kfl˝Ú˚≈Ø¿öjŒœ
·
?+Å™çÅy˜è5H-√kV=6eá»—e˚n‘¯úM¯¬Á ˙¿ZÍÀ }÷ßl|n¿¶¡Œ≤Âeflõ Ö¶¸Ëfi1EÏ∞%ëı]Âw∞Ø»ˆ;Ê˚ÍÔnflõXUŸ~ã˛ˆ¸-›ìı7#õ
`3•ìwÚµ∏≤üÒÂBìTo{Xï´Bl÷⁄¨Õˆ=Òœ¥
c÷‹Íä™
È™™I™ÂÖ
lŸÖ7¥Ãõfl9_˙˙∫
6…Û)@By·P
Ëq̘=∂Ô~à∞
˝£Ê¨#ü˘√
¥Xœ3vˇË`˛fiƒÚ£„ˆü6†ê€˜üåóøˇdbQç[÷Ôfi›æ˝Óùı-
9æ Ü =fl≈~V0õM¢?+nˇ≠`„´öÛ3nŒÔ¨ÈlflóNz?ÈœÀÈÏ◊∏
pˇ8 Ú„æ(@Ä_L§"
endstream
endobj
1987 0 obj
<</Filter/FlateDecode/Length 4033/Subtype/Type1C>>stream
HâdT
PSWæ!…Ix›(ÒF$ê{A∫Ú
QkZ+ë◊ÚP¡∑Ç!πBÉ&
’÷:Ó
2hªu;∂jµùgkµ>]-æ*TêZ«Óÿv´ÆŒÆµµS˘/˛ÃÓûã‘›Ÿù;s˛{Œ˘ˇˇ|flˇR0*?F°PD,\ú]T<wr∂XÈ´ùv[Å∏^Ã+.™v$§;d^2*§q*)<à√ó–ıÙãßv5|ßìTcª√C‹!åüBÒ”øfU≠≠s;À+™≥u˙Ùx∫ZìGVKºêíúú"§9™ D°®ŒS-ÆÒ9.{ï{mï€V-:Ö¥ JaûlÏÊâ
—Ìïü„ú
¡&TªmqçÕΩZ®ZIÔú±≤Ltóãn!√ΩfiæzçÕcØp∫Dóêñ/ൈ ı
ßW¨¨*ùv—Â
BuÖªj}yÖêÁtUU◊≠ÈOô€ÊÆ≤÷îe«
6óCXc´(J∑XÓ§8›‘»ÈÏ¢ª⁄F™ınß«·¥W;´\ûƒ§Ã¢bŸ…¡!Æd˝≠ Ã2QZ&…è±(ôÈ
Û√§Îò"-”»0Ø“p3L!„a3˜ZØ0+ÚªÁ˝8øù~= … ] k™2’U’èÍ8ı€Íª$ÜÃ!^r[†4ÖöÉöhÛ¥Ì⁄€˛¸Ì˛ohJ¸3∞ 7Å4=hy–˚Aæ†øgo
Óa'≥.÷ß
‘ÂÎÍtÌ:iLÍqÃΛ‘.=lW–5∫]Ÿ§íÜÊ
7ÿéó8ú Ô®·A;9ê7√ø”
ìíëòâtO§N˛Cy«≤“EHTÙAî≤O∫»ıí%*’õr4_ø€›◊pW
•aÒGúÍ}S£Ë†zê7T≈YP_äÖ¯B&∑c m
7AIÉh'§@J$
Û
à4˝«Ú±l©¬\ÓÑúÇBx!
íCä"L@n`ÃaL¡î0L™@s
&∂â¬Í≥≤À0@öK+Wÿ∂hgi˛∫ÎZ◊˝0HD3ı&T´ËÑs N®‡‡
∞xéåÿ]¶vó
`ñ ãvxá6’(6I Mı
áÜ6©ë÷≤¸•Õ‡ØÿQPO!Óá'
Ç
ò@ÄÄ;p`¿
N
”ÇLe∏fi©@@€Ñ©È3ËÇZ$ÙË+kŸÔïñ
_£ÄÌ‘ô>4áC5Ÿ $;„öµd
/NK∞“*ä˝(ÑC•
ò4iw£Âªo∫NŸrL€¶æ∏"flÜ¡÷∏Ãm8M+ΩKâ}CŒ‹>·k”˙⁄.\˙9
"Pu«·åd‘·î∑L#D`’µ^X
˛!{¡à`;ï,ƒÈœËoA-\„|ö#só˛⁄*vfll‡—Hpj√ì0!t_C,Ø?}kŸïô{LÕ˝…ûΩü|ficQÁCF'∆·ƒflö¿H∂
ÎÏ7vúqŒ·ı_Ωly£‡≠‚0çÜ“Jô˜ÄQ =˙¸¥‡ü(YQO‚pº
–¶Ê»Å≠ÍÌœ‚
“
HÇ
1Z ‹∞ëdèW√8rχ¡Ωgç7ˇ<7}ˆ≤‹¥¸Â'ª∑E0∂ÿW!‹ë
JàÉÒØ
¢©∏tÉC456 ãZG›ÔÑàAö`
6 /Ïìˆp†{Õ‹è¡F\öä
ig_ƒ|ZLì
Å&ûØø¥Ú$ ^p∞–òµ®∫ÿ¡76´oÌh„O∆∂OÌÀvÚ1hÊÆ Œ……s‰feÿzz|GªnÚ#…ÔÅ–ê„í{x,ƒÎøïfiì…∏1æ%z N¿)Sq˘kh◊B<iܬø¿nàÖqZär͡^ÁÖ⁄¡ê˜
’¿Q0¥p äÊ-ô÷ˆ¿˘„æfis%Ÿ≥.Õ *:3`“∑“€+\Êë¢æZS£F⁄Z≥8èvœdüEoÄ–Î{gÈïÈ »©<”˚·ß|a}ÖÑÈ≤-A6Cx˝ó¿ΩŒu∑ πxgOAy·≤’sÁ-˛∏À4(bvçˆ≈F‡ïü@6á∫›˜2 ÿKo¬B⁄≥ÁA>V‡§8T„ƒ‚=sèƇKOtU]6ˆù˝Ë¸qæπQ˝ ÷µhå6.)?qf3ˇÃ\∫≥∑˜ã„=}˝≠ππô+
Ryπ]aŸÛV mY*94c"–ˆ˝≠-
≠≠‹≈ñ°BÂX»9¡˚»9§‚EÇ˚ÜJ‘8
Æô‹√˜’òOÿÀ¥À`— º
làèz|‚Qf˝œ‡Ö~R…’”ÆÙ¥˘5˘<Œ Ù1ñÉGÑÜ^◊
1wKØN˘Øó∫ˇx§ÌZLH:E'
fi•¿dµXr°ccVaôªòG
a ÷C®T
°äcî√P扂¿Zã°˜—lƒuh@+
RP Î`ËËË»‹Õc<Ixc~Œd#F.Ä Z≈c;©àº’7?„˜<˚∞â∫\@] ¿˚©[ü∫∏û–hŸ·M‰Aãwó
(îʼnˆ$å∆î)E…<
ћA
–«XHxÊÑ:êéCË0G —yÚ§`∫ˇò∞ãh|?£ö÷ÁöÙÕœ†Éju–√Ô©÷6¬ÇÜ≤L¬á¥£ú¥ )Wâ°⁄¶fl }o¯A2`'˙C
—∑≈mûS
Û?¥n|^6c/ø"0≠
M˜p“ˇE∆7–“ûß`∫(ÙñöÍ≠ø‡ÈÇV§%2TB’Ç≠–22ÿ Ô˜ï‘<G-flŸ≈≥√XËÜX˘"Vr7h v´Gtbá=çœJ
5&Sbaˇï>)î∫:&fl/ [Gõ…
ePAßóïÇ
Öm≥aîDvbé≈¿TDéÚ6± Q&;iXÂ9/SŸÒœ®Ï+≠
5Z–fÇ3y¸r¥≤XÚoæ´=*äÛä≥.3
H¶∆a’ÏËå.TC°`ÓéJ@ÖT*>©¡˙Bq£â]‚É6»"/ëDûV$î·ɂçZêÉ#iLED â(A©QqÔêª9ßwÄ¥ßˇÙè=gÔÃ˝æπØflÔfi˚œÎ…3gF$œìêcπ€tG
8¬Í—;j G
£√?ÁcÈ`¥%¸p¨…¶˙ÃÓÙÜ¥Øw‹
˘ãSñ¶£Êÿµn
8›C7—Æ
˝¿
ˆF]BxË∫Ñ0 Á∞\nu¢LH9Å√
º°Çà´ùÔ+áΩZ|›/øØ
Ût&Ç˝kóH|;Œ?∑)Ô≤ÓjÀëã7?€1+W$>£ÿLπéû®E1
ߣŒ˜‹$ölªBtÛå…KEæœ8˜døƒ≈IvP¨¡LÆÄô|!1ûJÏ.—d¸(ñ
öUm√5Hp2≈ÿfldßmXEmà7∑flÂ7ï'åG X
KÄ˝ñâ
4éd>˚ßıOsïs>,:€˜0îmN¶Ü?É≈qˆ$Ed‰$F·ô®üc¢K2ï»
Ù®&éé\yäëyJ¿ˇ B©¸É°,眫q6
g0åÖb˚Ü
KÈÍË _CdKòhê]·mÌñ}~®^
W–¯˜˙¢≥˘‚ŸÉ3Àè8·¢AmsÓÒ≤&·‚È‘EQAŸ˛ª$ø›~&t÷MªΩj‡Z[…˘ëOÃL I Mvv◊ë¥ÛÁuP¶Åq8Ó®
c◊‚Kπ¯õO t€ “<æâæºwçM‘y ÖmYöËÍkÔflûÇ∫
¢!
’]
ëëÔ≈lî,P@MT˛ï˝m̨ı¡F„˙éoø;Ÿ—›}2ÿ_$glt'aÅZÂi¯^
ìR—Òs‰
ˆ¬±8
}q
5•…˝7aJ©ÑSÿ7R◊Ω≥PxuÎΩonU=∏‰ñ®|ÈåS¬í6J≥…:dž
,Ï•Õã+ Ë
BU#I¸tøÖ4∂µî7◊äY¨b¥S‡o˝÷˜tˆ‘‹È{P5€8bflƒ^cSYO¡˚Z˚»/„Îæ2]–˝DG0ÇsqXΩÑ/≤õSWoåÇ™wü‘ÎXüUq£W¯≤z]hŃ·ÁTëA˝Ω6U›◊3Ùr–@øg5{¶∏∏Æ¥$√R">◊dæ∑-{ªÄN—
gJk
fi=.
WÙÉì
.˜˘ÿà
ı∞æì$*ji∞‚;√-ö´õñ ù/‡ØCêC
Í€h&Ûmm≠h™ñ≤Ê≥s37,
VÆ)m‹%·4]Ú`Ï[OH≠è
ÛÔi˝Mùfl¥ øqÁÅuéqÓ⁄ I°jŸH|iV)_MS∫ıPŒ÷ûio˚‰
Éà
$•∑u=ËÛ;S‘1
(flú}ù.4?¶ÆfiB[W
ÈÈØ‘RFúÅî0Ç:m«∞“§îà·ZKQ±•H˜ø]|.…ı®∑◊j˛∞Ìœ[wÔÕÃN!q®¯?á√Ü? Ê·≥_(ñÖ≥ói§Ifày0Ó–‡Õ(˝v>.bd^Y.ª¥˝bîR
DÀEäØû‡8û^@ƒ»œm2A—ÅFˆ«îVˆÓ
_,‚íOiƵ›È<
.‚9íˇ•]%
∫,.6Al5EïG
ñmâY/Y(77Pß ÊFc…7¸fl`.
&À∑çÇF©Q†@Y^ k1`
h6Ç@†
–à=:`†≤8tYª
>≤n
¯ç◊÷ƪÑa⁄é ò.R ®i'ùM¥&—ˇå,v≈±+Ô∂
‡uãÊfÃÉâhà\≤}È&≈çGmd⁄ɵæõÔtK|gwUWfl˝ZC†»?2&È°ÌÎ ˘Ë.Txì“ÜYÇ/ˆ1ÖÂ≠˜O‹|Vrƒí^ Ú0I√[≥Swg̬√b#∂)◊ˆPqsjJ?QõÍ
ä$7≠¨≈)¿9\pó≥0˘aPU¿a)ËϺK∫”Á‘\:Ωsié≤)ø«Ω’»n¬I3ÔnΩ˚ÅÙd«ïùkt+ó'«-Y˛IkŸ!ïÙó˝™ &¥k»_©'flYfiflb
ÎqÀ¸]eufNπjM˙Œîåù¬[ª}*A˛≥~wJa
8z»FÛS(üP®«rV ø&d·ˆ”="4ê¸ï›Í
‡uµµ≤ÂÑòÕÚâ°@Ó·∏·öU yj˘êr¬ÁJìP¡s=Y≥24Ÿp2¢{`ËåzËÇ¢;ùı∆ߧÍOŸY¯åox∆ M: ±Ï˜òZÀ|ÿtñõJ
˝‹ ¡bVÌó詘;*Õ«Å∏ä
ÖãK†B MiN؆0
,цַhƒßÍCπR-ó)PGc–¶Î
6ÜfJà∞P
óºbU⁄K¶
SŒªYN˨I∑Z-Va‡¬±Æj"º˜€†Ÿ¶*ìMÍ≤ ≤…ÜßXöÍöõ}¡T»“`63
»¥Çp*ò0 h£v(∏üY.©d(∂„
·µ˝,î‰?…∑∑jF
rÇ享yˆ 9€\@?÷ˆë´+Ëã\_»t†⁄mhíˆfl
ág2J
endstream
endobj
1988 0 obj
<</Filter/FlateDecode/Length 2219/Subtype/Type1C>>stream
Hâ<U
TGÌf¨£
c£–f∫≈_T@DEQ@‰¸D0Açüq¶ëQ~Œ
‡Ä.¢DDADe4˛‘®
Îóġıåéz∆h«£Æ≤z<1∫ر8'[£{ˆtüÓzU˜ΩwªÍæ◊,”ÕÖaYˆÀò∏ËË»xüh)%K≤ı∫ÈR¶óo1åà±8fi
œ*˝∫ÂıtQ˙˜‰H0Y˙·˘áo<Î•Ù˛‚`ˇÓQÓå
Àæ˝kJzÜ’d\íl˝«èÁKü„˝>>G˚ä~~bò!}±$∆[Õ)’,∆§È”MÈ&ùE2å√RRƒYNg≥8K2K¶,Á‰ˇ)âF≥®-&ùAJ’ôñâÈItÕhêRK¶%íIå0eÍó•ÍÃ˙dcöî&ÜE˘ä“
}J¶Ÿò%•X≈£^J3K—ílJœ\í,∆”“-÷
âõt&´ï∫8⁄W‘•ƒTùU§,M“#Âi¢N∆4Q/ô,:˙^öi2ö
FΩ≈òûf
9*2>¡$P4HI
√“ãÈ•b8ÜÃ0C∆üa&úa"\òhÜâeòÈ.L<bÊ2
O∑ûâ¢S:&áπøõ
¬.bKÿ.ì]⁄Uû*㙕€¥nñnoQ*DÌ8ˇÄ[Ò◊©Æe9≈ÁîWÁÿ€
˙Œô]Î1l"W92 º¿D$9p][\ªÇècòD®çï
úsDúñö4—ªT¨
xïÕT∏
Tà®∞öîoŒÍ\ùÕZ§≤Êpw0úÌ\笱:œÆ¥⁄Ÿœ‡Ó3’ÿ…ë
D
√‡o∑·
x¿¨Ë§71ç&«I†ˆŸ*ÓÕ5¯åı*¢ù7èú!cSÓ“™˜f);[YË
7T ‘Œ9\
÷
^
ƒØäBÕóKmMqÌ™Eœ0B∞ù-T TJ_ÂWÇ£…]DV`òJ÷q2ÆÖ`Ù€Ïh~≠$£)∏k\◊¬ú±nb5∏;îÛVqt®∂x@
Ü’0Ba Ñå˙ìD
dæ7Å_
«áyì∞ØH$Y êÒXΩäfu8 €¡nQ˛¢æ
∏
·]D
·»FJß—µ´ØSpΩl4—˘éè‡Pè CRÙ
°∑»ó9Ü
4Ÿ|‹t)mtP¸å¡YF}s
äÏp∑u¨ÏÄS
ö˚ö; •òÉ—•§W¿
Òå$Zo˚w≤Exµ
i^¥Ø∏≤<‹À«qqõp
∏2≠/&SÚ‡Û… √⁄a(Ùw2†J©Fö;±?&
lÛí;é¥ønK&hΩV
IOë∑≥˘2\ìUv‡πñKªŸ™ΩQ~´¥nü[ ŒõW0?›‡6?unf
?oAU£–Y‹≠äõ’Õ|˝µº¯H}ÅˇZŇ|24ü
˜´˛˜'Ájkµ%EhA¡ÅÙfiVU∫eá∞£ ≠_ª∫p-øjuyUU≈°Õ{Ö£0ï
¨®;‰ı.†f(q˛-qÕ—™?1⁄+Cì¨Rä‡==
√ˇI∫Ûd⁄2íå#¬ØcaÙx“ÆáÖ
gûΩ(ú˜]⁄Í‘NÖ◊∑Â¥'®KÛÏqM4LÀvfl%k͡ÄÔ9¿Ì ˇ¯ÁYìNÜn§˛‚c≠≤QŸ∆ç≈ ‰*¬mŸ!˚‚x3ÄÑ‚~{
Ùk;ø˚÷y°kVX√ê;)¬$;
±≥2¥ *pÅ_8«ÅK-o¯óG√√◊ ˜CπMï•’5^0$˙Ò%fi¥x2◊øë|ìΩº∏FÑø6'&áÒë±ı€F[âM†µëdáævEcœÀvœîu≤ÊÈ{H‚:n“≤ÍÒÙÙχÅ3» “'H◊|WK’1
ÆspÆ/*¢‹û6Ø
; ìâChG
Azµ¯AüÊkUóÎzÉ2ñ{ì~ºÊEÏåùmt”àζ◊
fiÒ‡Ú‰€3Ç≠v«ÖÌ›‘].¥+≥˝…@û™¿C∆¿(ï(ÉÊpcpÊ@Ù;≠¶]6◊…±sæ¨is¬ÆB’∂ÛÂ?’˛›Ûÿ·sG¯ü´MãÚ~0¨—
”H#íÒÿ≥ıÃ∂S{÷
∫x¨ëØ?ñ™_Yh*öêátΩö–ñCÂg{=é8
%%˵∑VŒ©éÂ#bìf/äJê¶n˜}4—Ÿ>ÂVFˇ/˜u8æ̉Œìá´=è
9[›¿ü;aôk]ª®pÖC.”ÿM–à∂û(;æœÎ˘˜ßÜGL]ˆÕ"m÷‘Ì|Äú˛Ioªdx"´˛
˜üVèßcÉGëŧ˜»πWdm–é|Òõ Ùáòw!†ùtèhI
aà —“.Ii}˝å“*P4ühùk˘ÒÌg˜ ı¨9Y˚S√v∑“=≈{˘Ú≠≈ Ö=œQI~~Q> 8˝ªΩ‡§sÄ6‹ X-~‰„æF∂»0Séó?ˆÅ8Ö‡ÛØN˚¯¯|Γö‹ñ°’ºhMoÕû„53.;!"vˇ˝ÕTP§flÜ-Çœ¯7†™◊áëµQÕù®ÉQªΩ.\≠ºpÌBÍÃBJ∂zù]Èngû´†¨3Ä
¬À»àsC—
EõÍ˙‹¢ºï^1≠M{ˆîlfi£µ=@ππÖ9¸rSyÕˆíäç€ÖõpΩ≈;ÌhêÛO†s ∆›&kÍî]J%
8É
Gc¨·„GsÙ˚œ˛X~zÛn°.S%≈Q=¨—Ø3dz˘5Ë^›n?rı¥ñ 7#7˝Føæ¯IëXßîDMÜ≤ÜE˜ÜX∫¬im.T¬ë?æ€UâûSN.~ î•
◊‚l˜ìùí&±s”'¯íÿ5ä¬M (Ù_i≥˝ˆs≤Å
C∂@ΩOŸÑ3æ˚˛PcÌe[˙G
T≥(¸N;üYˆ=l≥œè3¬;~Ùç“c˚ù
÷Αk¿ˆÏœÃpS÷¨Ú“íTÈö≤âìΉÖ+j‹XÖw4œ^‘6_˙—∆CÁ∂ ÛUÕ˘7Áw÷t∂ÔK'ΩüÙÁÂtˆk\∏
˘Ò@ ¿IÀXı
endstream
endobj
1989 0 obj
<</Filter/FlateDecode/Length 610/Subtype/Type1C>>stream
Hâ<NAOa›mÈ∂`≠]É’‘9."V¢CZ R#V$öò4nw?⁄ÖÌnÛÌ∂XÑ#5¥$b!^ƒ{Ôc‚¡ `√Õhå—ƒ≥€ɪ
ú√Ã{3ÔM
œu¯8ûÁa<ìNç=ºö&ZÖX™,eHôLÃL[ µm~T˜41˚"oüÌ∞/ÖE6ƒOæú< ‡·¸⁄˝Ÿ˛fi√˘x˛«üQ£T•jæ`¡ç°°x?
∆„ÉêRå
ÅÈ™ië¢ wuŸ†%ÉJQ •i0ÂLò"&°o˘?®&H`QI!EâŒÉ1ÎfiTÖh9BÛѬ-ÀÛE…î
™NtHç˜y*keS≠≠
ö*›$
XjîÛòPu√™ñà
rT¢U/Ê“˝ È
•*∏))…´nNÍöT
dB-…ùse™öä*[™°õ◊ÔLœxOnÇBf9∑xÆõηD.¿Ûô…◊
/¨Ô€ø˜y∑_Ÿ˜ØwÿkÌIgM¿óÏ£»Üq3Ä?ÏΩà
qÍAG»˛√8Ã\.ÿ¢áò«"Y∆êΩÇ!~3Ë√åèD÷l%1ÅâV
õÿL∂XÇ%íI÷åπöNÒx{ØŸ‹.ı≈ÿJ∞o©§(K{«±»õä]¡˙xºÁæ±Á€èX4hfizl1·YàÖ0ÍTÇÆ
{1j'¯mϬ€~å„ÆË:W/ÿ™¿^±®à¨G∞˜FÔ€IñòÂ$ëÂF;€`xπ!‡€˙∑∫Ûa3∏∏”ŒÓ∞π≠êª9™;ø∂:1⁄ÖÈSË´mll÷jµp·]Õßüá#ˆŒ9€/˛`
b!
endstream
endobj
1990 0 obj
<</Filter/FlateDecode/Length 764/Subtype/Type1C>>stream
Hâ<PQhSWŒ5ÕÕ™±U„-µ+Èa4mWS4t-´”JÈf+({fi‰û¶◊&˜ñ{O™â≤±áB—÷ñ.Ã÷≠π≈Qÿ +{ä>∏°ÓE¡
eÑŒáZ••»¯oˆg∞s}¯˛Ô˚œˇùÛqW≈6ó
—æÓŒÆ≥M›45Jôöê˚h܈û` ˚«ïè2oVÏw{oÖ]ÔìZıûûôûVCq˜Ø•Ï
◊6AxÒ˙Ñ>í5‘‰#≠ëHk39
&ùä
ßd k2ö6Ièñ–ç›êUZHg*E˙
ÉI˙©IçQg¯6QM"f»
MÀ∆0—˘ô™–TúIjê.#ìNÀfbH’®F:£ÕÑ^J§2¶:JSYíRT3©Bÿê°gíC§W’tñ
°úƒ
Ÿ»íh:fi›LdM!i9KxJÉ&Uû”‡&U# j0ô˜
C55¡T]3[ù
8„\rÑ(t–≈k∑ÀÔrÛtıπû Sˆÿ¯ä˝◊俱q≈=^aèï>.èâp
ñ∞¶=RDÇw%pDy [co8t ◊¢}Gr:™™‰˚¥º`«8∑-,∏‰†b∞%Ap°∏v5∞∂pÉ4è∂∂ö´l`5ÿæ
ŸÿX.B;¥«ãMMÒ∂P®∂
Ah=»êÌÁ-Ñ°˝|»‹ñ€B ⁄†m
$»A.∂a[%ÃxîÒ¬flX*Äø∞^ÿ≥l}nΩ∂@±@¥.Z~úˇ√>-ÂΩˇ<Ñjà¸xB´ `e$u∫ÒTz∫˙ì,˝ôæœˇfl<¨ (_'WWa◊3p?Æ}Ù”˜?‹Ø˚˝ÏèΩ¡¡
‹;è˛å≈µ≈_˛|≠|Óm¯‹pkéy∏
wvú£∑Œ^ǘ©8s„´ŸoʆÚ∑ZÁMÔìÔ
º®É⁄Éœ1å ∂
™.œñb≥ˇéÃàı‰∆t˘fi¥77WäÕ·Ö¸;pkjs™¸*_YÿnÌ∏9±>s›©YüÔÊ$‘~1ë˜Ì¸_ÄÅo
endstream
endobj
1991 0 obj
<</Filter/FlateDecode/Length 563/Subtype/Type1C>>stream
Hâ<NAhAÕ6̶⁄R—≤X¨ƒ(T0≠1zH©•âPk”T+*ÖÕÓ4ôv≥[fwS#^ºERR∞=Ù‡•={U
RP/BØEP/µ º¸i'†ì
˛√˚Ô˝ô˜xJ†Ω-†(J8=ëIçŒ\»´L<j˃'„”9œ
±é~~Ö˜∂Û≥›öHà«áflov‡è∏{Ú5ˇ|*–¶(øˇ\w+åä
\Jƒ„ââË^é@,çA tÚr◊#%nÿÜ√
¶{ƒ
Üîe¡TÀϬq +∑éˇ˚uAèÈ&)Èlú9˘FMb +£Ã7J∫k©MlH•#@
ñÔ“2±*`QÉÿ.1¡+2«/aú⁄éWY$í‰ôŒ*ê.Â3–mJzdKF
Tˆd“Dm0ÛtπÁ}F]ì
ulw¯‚Xn∫rL2ê”–AEôÿ¯ ´µˇ’P$4ǵv^=òlVU|&∂4ëƒï¸©
Ô5lâf=‘Tgè8&Ö‘*ßµòh©ûÉh
ìºc [úƒ,ŒÒ ‘æ=›‹⁄ÈÛ øõu
˛πÿÌ¡;Ÿ´Ù¡Rˆy¶ìÔKˇóeOÔ‡»
;ÉÁEh[\∑Dóhπa˚≤åaô‹∑§‡.öA‹Â5MÃàdHz?jhbxìCºO‹W≈vSÌì¯)‘Ûh˝`v]◊0梂ÊJ”X
˝;ÕØv‚F}øfi‹[=Ü«Ò^◊rwœ_O
endstream
endobj
1992 0 obj
<</Filter/FlateDecode/Length 1738/Subtype/Type1C>>stream
Hâ4T{TWüa23@1Vb8ßvf⁄ÍF„
∏¥
÷G∞´%*ÂπLƒ!!ƒêW™VyaƒÓ.6·a—ï≠–*ÖjA‘=XJÍÆ«nÌi◊cÌ˛·⁄˝Ü^ˆúΩC€sœ‹sø«˝›flÔõÔ^íP$I>ø„ïщƒ‰U€w'lsöä
≠EØ⁄]¨˚å.Ûö≠õUN$éî"“ج‘(5˝X˜c
ùãat…ıHˆïpÇ"…ûæÀ vGô”öw¿%Æ˘•fl¨∆ÛÀ˙ÖyÉ∏Z‘Ø[ßflb∂ÁZDcYâÀb+∑Ì≥;
vß…e1Ø∑ä©ÚÊ1’Rbq∫e'&%˛¬J¸âñh-M¢”íg≈(NãYt9MfãÕ‰,Ì˚1&vô\V{ë©P‹]Ê∞Ï7Ì≥à ? Ñ›keMQ€årLåÕñ˝A‚A,&
ADSÑÅ ∂؃.ä0ƒû "ù "p±à$"Ö0ƒ}2ù,'? ⁄‘I)®
™ö˙Ébâ"[—ßx@ÎÈ£Ùy˙_\˝àÙxуÛ≤™^!
üKô?Œ@W£ç–B√CâËödcæôùgr÷∞aõëÆ™Âí-e¢2±
¢»iXOAYD°ı(äU&v∫Á
Ú6ƒPppŒ†F1ˇ3@
£Ñ+ùnC($ÄRéÇ‚p¯’¬<E~∂1HcÙùÓÀ”w5ìÖì∆~˛¬fi]
I
\Äên)ædŒ]9Qfi-ºSy¶»°±U ‚ÀãÚöÚπh|B•TR,!flÉı`ÇXJî˙‘åiÂ
„v¶Tö“Öå\ßqáÈ ,îN~Õª5©ö‘§ÚÏ≠iÅièVXi§yBå†Ê¶f⁄fl Æ
ÙMLj>µ^«|2˚6ü6∂õõì€F4◊ÆûzˇVøÎı?Û N∑4ë$$c’“¨zæ EÇa~bp`≥¨fi
ji¬C^‘OIèÂ⁄Û—L^SÊ¡Bfi·…ÚpÊfl∑^t
ázÆÙi§hdòèfcõ‚?M·3GÔ◊Ls3˜fi
Æè’›ù—(Ωwπ·ÿù'fláüÉu
:UÖ‘q8PË“ÄóΩÂK‰/‰æ⁄ñ∆â(,-Æ@®¢G¸CgG €˘é“⁄‚Éöjv◊—∏cØ
NtfΩ±Y£^ıYÊ7≥ Ùfi
‰Uu≈çéì≈¡ïP¢V
Á5ÿ‹|qπ„êçÀ-ÈætÁI˚ÿIAÈÖE!(»
à«C§§ò≈E˜ÆôE°
äYÉh¥ÈæE$¨Ög Õ@xõă:Î≠‚‹4.∂ÓÎø›n˝«Ωk˛úl
ı√™Ô`˙ ƒ{∞¶(–ÉV5åUUEÃêU∞Cñ∑S9¥¬ÇV¢EÇjÖ^B"ºx{/ ˜çå™"û=0Ugù£⁄≈ª™ùeŒp¯·Ë≠&˙rÚDl>„)h
¸
¿)IIÕP¶nò™ô6çèõ
}[9§◊£EHáV˝˚yX
õoÄ. †»V:+'?gáu¯&fl†Î
®«}Åos|cwì†q¯<ü¿
‰(h)»ë|j§ù˜Åñô€©¿‹_¿+9Iær∆hheQåRJ«[óÅ
-à?}K#U˜Ü1å
gŸ—„≥_ÃzªóGgl’pw›•S~fi™ª£ã{◊ˇfAã‡+≠M˜h>c?j
∑^‚/⁄2Œ‰‡÷∑'
7m¶ûDn{ܺÆeT˜Ó≤rfl.ˇØ!·#xœØqπ/è`b–≈Ù5ˆvÙÚÔ¥˘1¯ù#õ“‘Ö˝ìÏï˙ ˚_˘[VG&∑≈T¯öMF˙‚+$∞JÔ˜’c≤óu#Ë)Ëî:‘(jb—
§˝'
≈=™{,,›E—BÉN}¡_ïfl&ú∂4fÓ”$
”怜éè˚
˛ùW:
zŒ~≥ÍWM›¯•{ŸoN
䣺™ ¥¨≥qáœf¨ÿÛ
¶1ıàU∂{!tÉ[‚∞§ØÒF<ñN™qÎE3h©∑
≠§ı(‰>r1™˛Ù˙§+Ô8?vtêÎæx¢πWä≠-/≠≠‚væ’1)@êX¶J!-ÛÑåÁ©J•Ú…áˇj´∫\‹X‰uÒ∂*{i>óvÏΩ>«ëœŸå„ô=ø„≥{?®˘àõ∫z~¬/‡-çaï@/H#[$3% çB1+–ÃJò¡Ö¡èÜè∆/"˛50‰ÜjŸ&˘(È∞úßb‚ <ç61∞
U£x‘E√RÊ?ê%–∞âAõ†ãVz[Á
≠(•ïÅ¿…˘Ïˆgª=X∂Û!¿ÑLj`˛⁄ˆ∞E
aJ©©D©ˇ/¿∏tø
endstream
endobj
1 0 obj
<</Annots 154 0 R/Contents 2 0 R/CropBox[0.0 0.0 612.0 792.0]/MediaBox[0.0 0.0 612.0 792.0]/Parent 1968 0 R/Resources<</Font<</T1_0 2003 0 R/T1_1 2013 0 R/T1_2 2015 0 R>>/ProcSet[/PDF/Text]>>/Rotate 0/StructParents 89/Tabs/S/Type/Page>>
endobj
2 0 obj
<</Filter/FlateDecode/Length 7502>>stream
HâÏW€n„F|◊WÙ£
åËæ_Ç @‚LÇyí
ÿ
éDç∏´ãCQ…xø~O7IIªŸ-a≥
∂.d±œÈ™:’wflWuπ»g5˙ˆ€ª_Ó?¸à0˙Óª ~ºGúi…A83ö£ÍÛ‰Óc± ÎÚè‚~ª⁄VÂ∫®´rÜ™rBu¶ë ¡3é…å1®*&ã…˚_Èn“=ƒêL¿µwá˜$∏Ã0¸ √†
Ü{<1:˝ÒÏP#≤? Ü%ö¸n´Ö Çò»îp%Õ÷Ó¢ıDÆÇW´…√‰o
èìª˚̶.6GhfiáÜ∂
}˜H˛aÅ ÂæPàIxîÕ)z\On~⁄VkD0«ËÈÜb üno ˇŸ<Á˝£ßq|PoÈ∂uÊlÌ‘d,ætŸ!∫wÀÇfúR∑V-›RÀ?»ÆŒVEö™HS/¸
gúü^Oï
û©∫gNɪ8ö!–„|rÛòA˘fé‹É∞˝
”Êõ˚™òóıÖQuá™›¢4Z
kÇfiPm‹¢à
flo∫˚U&;BDF{vÖ]⁄ΩΩy∫Ÿ*7ª∫⁄œÍrªŸ=›fË~YÃ˛Ö ÙÇ’vçÏn√µO∑flåîAZ<it∑
™uøûq∫r‹]˚ƒ§FµY©i¯ï,=%
Ü]˙˘!
BÂ
dw§`˛lõtº$.üÆ~ñ!{
–n ȶtìv¨¢ë˛…AˇWÌ
í˙ßzÇıfi
ÏúéwŒ§wN‚^fl∏Q#
•>
€∆∆€Fá¥c¿k–©ç£¥fl8ˇÌ¡€˚¨Û\¿{æ« ÿ†sá&ù0OhœåâU∆—ê- 93d&A?=CˆÄ „$~»vëó¡™!óŒ∑\'1.:3«•lÑHܬ •6¸…∆˘√p`ÃqMΩ-†q¨Ï@ >û
Z
qD≥s>áÌèÃNF{$Ú¯5◊2
Õ ıl†
Åè‰T4)Ïr
ÃIG—8ãòí”≠PX&ûµQqïQj2ÂßÊ˘†g<£mèUòíLüz[Kmöòu
;ø_o˜pΩŸ≥e1flØ
Dfl°Uπ) EZdàÚîÀƒ5ÔÌ≠˜Ì’M?^®sÀkıŒ(Pü^¶wé√N⁄»
E9'¨Ñ—ã˚$Y˜^Jz{¡©_ˆmÌi≤Á,‡úù‰œù3Eˆúù≥s$Oœå”É'¢äÁ2MÒ@â]uXÚ\≈$?ü;yÔl‰≥nŒº…¸Ú§œU˚äËDG¬d◊Àå¬Éhè¬◊ó'Åì
¬OaoÈbò´ù°‚4{t‹o;ó`
‘E.!ÿx8Ä^2≈#nÎÅÂQ≥"Õ, ? 2ò õÖê≥∏_ñ´9™Û/hVÛ≤F€™{µÄó€zYTh^<õ9‡ÓŒÇ
X©£8√Ø“\FËß" √˙ÚX.tP}_ÀÖIüüfiÍ%ˆãØ-:MÄíDÊÛ©y•®N“¿lNiûéE’&yí⁄§—]Ú°8,6)Æ „¨
„˙-åˇ˜‰-eRóF^
∆•äÖqê—ua\ÍTµ˚)ÈÔÖÒäΩ´=MÏ
Gƒ~Óó)ÇW$ x£äW4™x≈“ØÂ!…Pñº‚Èa‹∏0¶¯∆_ÉE(ëfö_fJFÏ¡
œìƒÏA©d{Û◊fl̘ÕSΩ¡$%qiƒÂI\„—$n{yM◊$Íö¶9Ö‚áÿEiÿ)4ã8≈√˛S]Ÿ5∫4@I‹¢3ÙaÅ˛]T[õœW≈n˜8DÛ)û:?°¸´3î0c5 Ôòuqx◊"fiA ◊Öw-ìıÍgëøzÂ◊k[töfµN”Ï©˚%È’åÎZ…‘†óQΩ
’´!izïÙúXXÆÜF‰˙kΩ˘’˘ó¥Xnf´˝º‹|FªbµòÎÁ’ˆemÒ‡ÇwgÅüæ;H‹>ü5‹|≈r3,mRJ|yò6<6-Åu◊Öi#í’ÁÂÑø“/æ∂ˆ4Ò5
¶˛ï¢<£˝a:–¿hò6&*9ÇqöÊê¶K#<,:ÇIrú¶¥â”,CèÀrᇘeªØú§N∂˙¶fi÷˘ ∞˚¢EΩi∆&~
‚{}¢'òé
ŸÜÒûõ0 f…¬‚–!q
Ê~irù(KÇ#GÇNû¬\
d ü
:π&…¨z:ı]qúıa
#†
˚W†è?wvX≈îs ü·¯¶øêÊ-¸cI&3Ev;À›Ä‹°; {97¶èqIå!ƒ
Âßb^T`0¡∑ά˙˙≥¨óÀb5wc˚õÈ»Q%@
ÜNˇB
⁄ébϸúÈ\≈âHXøô∞Kŧ{∫W)Ûñ
åπ\ü«\¯$:'›πùw¨n+&’-#ÉÒ¥‹$’òä)≈zâN¥üË
ɢòi$©Ï“E>FU„°*…tG‘mµ~∫Ÿ=›¢øO©ç¸ÍN|—$£8¿*cF´(ø<∏JÜÃ≤Ä⁄π\<qy…Eil42C3-‰)´®»c
`ârÇ≠Ê€“$„ô ©p ÆòR≥¿´!e<æR5
_[˝~!ü∆∆’â
Üaifi$|ëÑMD¬‰R˘2
î/h‚ dÀHä|ÓìääOëÚ
Èó$kó±êv…F 8J]ûjY8N$µ—6É´!ÃÄ•ô¶á‰9Ò6Óø÷À¢B
pÑ
O(
†ª∫⁄œÍrª±·‰¡ˇˇßc§Óizx⁄ͧ›F»À‰Õè3ˇ¸¥’™
àsá«-/Qxí»›å>!
≥H?xP‰«ù"t
˙©W&âúÛ”CNøõ
ˢ.•ã‡.µ&í≤K>`ÙêkU‹Bx‡h–∑apó‹ÊcqÇè æüœ—™‹;˘’ÀjªˇºÑ◊≥∆;Ë[¥¯Î-LÑNñΩ†
Vs˘…BxN≠
Ä@Wû,DÙd¡µÃÓÒìäy¨√ìÖ¿¸Px¢eâ–π¬b•ÌCq…
9.Y´∑ı(}åkrD¥ByDK3û€Päb∞öbWóκ.Ê®Œø†Á¸e
;îoÊ(_o˜ò??ØJ¯~Qm◊Óa–¿z_mú∏~ï‚
£â
JCó+#∑0q^kòZ4¥á˛KÏÁµí©úñ$»ifß®–Íäº-È–:¡]ç%ÎâƒwÖ'‚3fô>;1pÂxy†'fi7pBúæŒ3È¡»…ˆVg;¢]Hâ ™!"µëÒzD
Bî∏_2 ¬˘®!éS†â˝3á?i∑·Ω
•âÌ≈ykÌC¨# ˜ ÉÏs∆ ¢pzüõ¶M
¢©"ÇÓy~éMª•Í¥Y¸ÙºG^£P‘ÔÙ'>-ù1≤ˇõß+ë¡
úe|X†óÌ
-Û?
î;∂€üÛ÷flÁ´rÒRn>£Ÿ≤\Õfl
/…Î:ü-—√lô°˜ Ócû©Ü£ró‹qéá*…âTo∫í∂pXqŒvh2ç*OyÑ‹bµ+
¡ÛoQ`{LΩõÀR
OXjd.´ÿ\~üWò∑Âf∂]hVÛ≤FO7∞OO∑_k¢
#_h`34¬≥≈I…VèÃu„≠“s,K «3"≥˘7@4®Ø9@vï'∆MC…ßAK©€
€˙®zà
ù˛ÌÑ’¶/"\
î√a"ŸÍ∆k#iéúyI1¥gä∑ã6ñ(¢3W´¡˛πí]Xj
Ü-L*7§Ö.…ùñõî‚¥GmºåÎUÅ¡~Î<˜Àˇp_m=n„V¯Ω@ˇ ß@¢ÚN±/A∞€Ew ∂A&/ã¶ö±&#‘∂
IŒt˛})—÷ÖiuŸ6ôxbA:"ø€¸2€Â+r©âG.!éπrƒ*˙®⁄˚
ËeU ã}ov∞T‘Œ0‡zÂÓº/QûjfiÏJQNK&≈zΩÕ◊ÔLuàÕNµsÔmË◊,(ã 6Tê-∫®y≤.zAhÄ…‚∞ÛDY‘rEâ«_íx•=—}êë§F˙Jz≤˚’∂ï‘̈ù
≈â|ÊÙ:”Í0°)ˆzúfi ¶z,é®>ùͶ; ´ÓuB‡ ÍʉïÏ
⁄WG‡±eiœ ≥l∆"≈12r|)‡Mπfi@Dä”âË?Õ¿ÓÉLÑmß±ê‚
ôN_),§8ì§.˙JÜY∏πd
I"
æKÜWXHb,¸X∂eÛÊêß∫AOÁÓ‹îË‹ñΩ!ã‡o>5|
„•$∆uöfl>èPÊ;«€ÊJ“ÈÓáM†b5Œd∫êH£ˇX@ì®O¬‘Oi®Øbò˘[+&ü&ü‰.91≤¬{wfl˙|ú'eÁ¥pñ,‚73ŸoBi:°¥A2zÒ1õ»€#5•ÏJO›‹R≈ìfi$ÂQÜ”tÜ{ÒhG–œá$íö∆H=W $bS5ñüiC]·˘A•ŒÉ5G“A˘*Άrl-…p\:Iì,/Yè—Ì`4¶
ªù’âQı—
˛È7®8Ó#˙Ù
ëê#^ÎscÖdÿªÆÓä=™ªÁ≤Aß‚ıØnÌ≥M˘t>Óä–°~
h›£√Ól-H¨k¢`·j∏`ÔW∂
q%2:iäɱuπ0h1(Ñfifi&å«¿ˆDé`"&
‘H ¬C†r°¬bäß™Sï∞u¸é[+À¯°ì¯¡5œî
GlÖ
ßÛCÏÄ
r M$«Ö3PıˇÂ«úÑå£g◊tCƒÊ4ò1fl±9KeïA]¢(–Óeï€w"≥∏X◊)Åôπ6—©$߉2®S˘3¶˝åõW“˙Óep{Ü
LºÂ\¬u
?À
ê˛+¸ë„9ŒrIÏÒ}¥ÜÑVî@\î`Æ%∞V√¯ZÅXLˇÒ©O‰‡EUã5G˜\
˚ãîøAÌ˘°kLÔÜ+}¢ û1zè¡œÁ?Ç·¢¢˝ =sÂa2Sƒ˘f˝µlNEµõÎè»Úúm£∫†™Cfloœ‹Ç≠¡ƒ∏R∏.¢a˚¬uÔ)∞
€ñÍ√æ©.BQ{‡¯Ç
I<jŸFßCÒ&˙
&∏≤HteÖØ)E¨PI^∏xW¨›c‹˚û#µ#
∑ty)‡⁄‹≠˚ƒZÓPWõõÊq5C¿fi ÍÊÄr¯cXXt]Ò¯\B&Äœ«!»¿•≠ rãˆ_›a%]†éKìÉπ‘P$áø´xììÏ{ˆ>¸,詺A˙-‚y–ã+)˝∏ÚÚú(5≈XΩÚ3YÊ©,ñyÑ≈J€"∑±Xz¶O'1õ≤µJò=U`ˆ
Ò¿
`∆]ÖŒXàiÙ˜US¬€v©n´Óùi:xê
nŒ°ÑL
@ñ)oUÜ©Ç
ÓÀU«∂kŒè]U €lÖ˚j2ÿŒ¿@08?º0øƒ∑á5ÎWã#}>∑’àe ®⁄«˙‹U«/Ëx><îMlˆTÀdHfÅ∞@®ÜW÷åÿØbMâ÷L90•æfiÑ·flU2Fmu! E?°ò¸H˛â—næÿêîS∞xö˚#K$Dí++O€
zËC1Å6o,òcOA≤Ω
ÒîÉ”‚õ
zÊ$òH∂ IÓIc`Û€è$ÁûÇä˝G‚1
#¸[À…e9Üi‚ëxı4W…Ó≈ 4âƒ<Œ˚›ß◊S˘óò÷‰˘BkòR∂∂≤ç π
ã
6åÔ…Ó≠s “TÌ1ú‚dd}tO¿p.]Ål>ïÒÔL‘2 iɈd%&“õ†gYi˘lx„<a„b}„úÀ
ÓãØ∞Ì6∂Ìk^ÇÏ„›Ë”¥†œcåÇvÒ¿ƒ◊õ†v„Ê<»>∑Õx⁄#Ù√¢$ÏUL8∆dî¥Z/ù’,’F%f'±»&∆ë¸6fidJvcÿ#ÓC®åm—'# B…22‰
@œ0 ÓVb√˛ÿ√fπÁZÌ˝„£ùß˙ÿ≥éEÜÉ©|âzJ»=
«rœPÒ
F.2?®XÚa8=˘q£„0
N=äÖœÌ≈H(Ìl(N:äÖSŒÜb·Ñ≥°X8›l(J6JÖSÕÜb Så»ç̘†ü1≤±˝
Ù3–ÄMÌß
Ù3â7ïÚ†ü)æ≠˝‘É~óên/ÊA?«€‘~ÍA?'*°˝^√£Åt‰1<M2mΩûg
bLä…À£“ky'ñ7*˜˛`-Ø~B˚ÍX™–k}F/\s}X”]q:Ì´rá∫⁄‹”IJ¬N ∂´Eg.ˇûE˙KŒÂ,À%õº◊VánÈ0˙¥˚√]f.õ?B_W‹òN≤‹(’/∞zäôûÕLdçû€hˆå9Z@pÏLüüW`ÈÀê«âuê
s§<H
V∏ö"X(È
4i„æ∫
í
‹\í∆í ÛÒ˜Ô//|€O8zvå˚9G˙Ø
b!ß/Âò=JaWô¡∫‚/¿éøøî+
dzœYl Á™GÖZKÆÃGcöiB:‹ü ∫∆4¨'-COM}ËøPû°OœUã‡ß{.ó,ÓwfX^˜˚Ω„.ªÓò⁄7˝P7hWvEµoåxœıã·ˇ©x}Éæ‘ÊøÆ
*ºººdU”f_ÍØ˛Pº
`c̸-ä∂eâ™c€5ÁG3<∂∂3ë"Y~≈Ø0CrßD(BX∂67ZÄŒÁ 8C@§QÅ·†a
è^†[ÔR`ƒG3öÙÚ¢a÷\ï
$Ω{!‡Ps]8ôÏÿñ¬9,ã&/ãÆ-
∂H≈B†÷≈&Â=-
êîÎôŒØfiùØêûãÈˇ:∂Zt*è≈æ{EüÔÊL˙¸'ã`í#.m6q.gi¨í”Úzîîfd*¸æäæHflÁÄÂ:
ˇ¡'ÁsˆtyˆÅ›árÄŸv"D0@%2Ά¢ˆd÷;(¬Óü‘A_…®˚ã
˝@ó·À¯”—¨[≥!JËI›·+¬
›·XŸ"∑aLx∆Ÿ¡ 6wH.dÒѸI¿§<€LÇg†uzΩmìû°V(9≈Ë[¡qBºìÿØ≈⁄J†Àw,Á.flABjvËC—ÄÇ.2fi˜e[}9ñÂZD샣÷éˇC“É◊âL&˝} îHñcßÜ&Åôkz.z\Ê.öIÕÜãù{ñ'Ë≈~A¨ø1ÁÓ‚±Ü¿◊ÙA*”ÃΩËT6-D∑˛≤§·™ª™}<∑Ì¢@g‚‰∞T˜xSvÁ∆
m†Íûá[ô /œó√ªÆ5¸xˇŒÌTπã˜Cœfl2ôax
΄
g≤àä2”ø;˚_¸ä3C‹¥∞+i»ïîÄ2–ûØÀëd9Ú>} §_±‚dP0∫G¯…ÔÀœ‘Ã5L…åhÀÀ_ 6ªå0n<˘Æ>úˆeW¢áhñE[$ó˘öÙÔIm—T±ΩOá[î'¥H'∑H–IÉ~ÆWDPaè*[H9î<ì0eX
tı3•¥
…Æ"ä«‚P¢X≥Y4õ@á»`=ç”:2Ó∑◊0]4ƒ≠õa,Fβ\ KœzÎ,æ\∂X.cˆták3Ò&¨w9l∏ı¬Ï5]≠ï˚bè™
î®û™«¬Çaπ˛Û·Ï‚Û›á Üô!∫±Ñπ &Çfl2Ø©I∆7ëΩ,¿–õ[SÄRQî[ˇÇ˜Põ8∏ Ϊv»D◊
9€˘[Ÿî—∆‰°±EòÌQa⁄—*¿‹¥NŸè^
3éôM\1ôf?’<flÙ∂™î3Hc’Ω
(·Æ
fl
.*»PK©ˇ–^uΩm€PÙ‰?12M§Hä‹Î⁄¡ÄÆX⁄áyQm¶vk[ܧ4ıøfl%E}RôdE
GÚ5yŒ=˜ú
°çMÍŸW8~éËܵèÔfãg2/)†§ ìÔòWF«'íà}ˆóRgT†Myæ†á≤ÿ ]`™∫À1÷Öµ)ÌÂ$Ô”∂
mW—è-ÆÛ‡d\QöH Ãq>ù∂ è≥-5{U£Ú>T_ ´À
∫E[µ9–
ÕÆh‡„ƯÆê˙Q
˜'µE&1ŸàT‹_ù∂®ÿl¿Uä”e˙ÇÍÕNm P≥ÄGuS4Í'¨oÃgHf:1}Vu£ÛxAflN”Amø‹_)Û∆
∞©Ωz∏—fl∫ s¶ÍQ›éU•6M[tc=-Aoá€ô†ØT©3|GœÅ˚´6@¬ïN®)~úãã™`2¿]>5\
æ…8vé}Öß›~≥ÍÏä›_¡M˚c´$† ·u ôDí+z∫`X®¥àà
èA¶#f6a†rFá Ω,ıO∞4ºÔâÛ[HÆ«xñ• ax≤
¡üf´–¢‘Ö;flçÊ«fök<à∆°ïÀøZ⁄Q
Ë≥‡îÓ¯∂ß∂@0ùÀ¢ÂûyßÎeÃE*À0¨π
kFh$®K÷◊Û‰ R
O¶(ü∞Ùƒ
‚F¶nJ–WÔö ÷!Eçƒ>+"ôˆ"∑È≥<…Ç‹HÚ*n
eé¨2†àåW
ÂfÛx
‚Œ‰Æ
(7–Åé¡ò‚@˜ÈAdK†CÈ<
˙Ç Ï_fiøR¨£J!H∂∏ÍlßqΩ}0nt˚œ
™u)pa0tk¬esy¶∆ç>Te£L @,oºÆ∞o–ÆÀRì◊ÔØk#∞ökr9ÉZÑ„2(M{πYó!∞»<√ahÍìôı"Â4¿Fz
MÑ6LiBÂ
8ßiÁ-D∂òhw. kª®ıì hÜ}mS¶I77ܱQ¿æ˛
¢ˇ£ç´◊«G»2∫N`ò¶‘cSö£Xã¢)[∑(á†ã¢)˜å¡(nñ
.H¸ıt$fiZ‘òÏ㢩´<}u£úX{¢8]∑'W71ˆD1~/ÇòÌâ‚Ä®¥=˘5∏TtÏä°u{¨AQÏSÉ5(ˆÉ¢xAÉáæ∞{qæå+Od6Ò(
.aƒÁQêå
‚⁄´
œÈÕÎ'z≈b—´4uë>ÖÂò∑T+d≤…∞¥U
TÏ댡hÇÃët“‡Koå6≤˝‡ìLòÜÓº2Ê$jõ‹!÷-…†AõÆÆ=ÒÛkÒs~‰fiè†ˇ&-éI¬·{´≥Ö∞l!<“∞9Ó„Ôá]yRËT
ñ‰>ɵPe)óç¢V\vL™.∂X"˝îvUÁî∆UŒ“üChÜ√Ñfƒ7‘`L\yƒË€c±?†bª≠T]¨.ú†ó¡(áa{9‡ R–+m£˚-F[
+cõ⁄’π®`¯πè>¡˝˚t∏Ñ:+s›™õöˇ
ˇiˆV+cÎÉœ+n(.
qªÄÒ <>4Jµé
Y:»—¬Ÿ˛©8VÊ⁄á5–¡Pq¿Iü"µ£/hkMµCW¥É€…ëÂ|"
8-á9≤{ä◊G
´Ú„⁄o&!p)q¿ÕÑ–†ºÃ(/]ö≠∑•.…@Üœa√°~√±G} ,V•i∞Œ1+Ân:•\ohœ5_Uóƒ/UxAµGçuQ
!,]Gù∂ÎÏuÙ·„Ì˚Í
;®õX òÉôƒ Œ»:‚]¨ú#
-YÊE‹
ÛÂMÃË:ú,ù∂ ;µ˘Üˆøáe.†ê~Kˇ÷¡‰ìâÎ|ÛŒ◊A,èË ∏2—ø•ij˜†;ux¯U
œáÚ¢∂°kKØ[ì6›g\&$2ÂÛ‘c<ùUC{Å
Áú˜≠>_0°‹BVõÌó.ÊúÑ1ÁŸ:ÊΩ€C€2€jÔˆ’1fiÈπõìÏ≠H∑V±$nC‰Ãª.®≠h
ª.õáAÁˇ7ËçŒçò|»£˜
ÓÔsúÂ<ßœÛPü[
ü›Î˘BØw5Ì95
‡Ûànœcª
ò÷Û{⁄Ì›r‚ ˜vºΩZ|«Á°éü◊ıπßÎu≈9¸ësØé‡àÑ·g
)| (!-≤˘ˆˆ}êI1È<À©ÌéëJCc=*H"ßx-º%õq8Ö
]»¨«˝Y¢¶4«‘´iW±Îßßßd_’…óÚ˚oÔ ÍàSövÔÿuÌ=î⁄üͶz‹h‘†O[‘Ï:@⁄≠xo
˝, ·@<m»∞0quÇWó1»&pSïk£O∞$-π%Œ⁄„Ä€;JÛæD,À>3~øÉ§Ø ]à…+hŸ˝5I ΩˇEˇΩ
9wø‘Aıü.±7b
endstream
endobj
3 0 obj
<</Filter/FlateDecode/First 6/Length 126/N 1/Type/ObjStm>>stream
hfi4ŒÀ
1
@¡V∂Ñ]àmpEÙflhôúû¨8#_±éÛxÁ _^GÆ“÷˘7Œª±¬|ÈCü∫tÔqÉ‹‡Ê©º‰%/y…K^Úíóº‚Øx≥fly≈ˇãW{∂flºÊ5Ø›◊ºÊµ˚ö◊ºÊ
ox≥Ô„
oˆ}ºπΩœWÄ–FQŸ
endstream
endobj
4 0 obj
<</BBox[0.0 0.0 8.0 8.0]/FormType 1/Length 24/Matrix[1.0 0.0 0.0 1.0 0.0 0.0]/Resources<</ProcSet[/PDF]>>/Subtype/Form/Type/XObject>>stream
0.749023 g
0 0 8 8 re
f
endstream
endobj
5 0 obj
<</BBox[0.0 0.0 8.0 8.0]/FormType 1/Length 43/Matrix[1.0 0.0 0.0 1.0 0.0 0.0]/Resources<</ProcSet[/PDF]>>/Subtype/Form/Type/XObject>>stream
0.749023 g
0 0 8 8 re
f
q
1 1 6 6 re
W
n
Q
endstream
endobj
6 0 obj
<</BBox[0.0 0.0 8.0 8.0]/Filter[/FlateDecode]/FormType 1/Length 82/Matrix[1.0 0.0 0.0 1.0 0.0 0.0]/Resources<</Font<</ZaDb 155 0 R>>/ProcSet[/PDF/Text]>>/Subtype/Form/Type/XObject>>stream
Hâ*‰2T0T0¬¢TÆpÆ<.ß.˝®Dó$S=3Öê4.C=3cC##=CÖê.S=cK#
Ö .c;Öê,.◊Æ@.ÄA~q
endstream
endobj
7 0 obj
<</BBox[0.0 0.0 8.0 8.0]/FormType 1/Length 24/Matrix[1.0 0.0 0.0 1.0 0.0 0.0]/Resources<</ProcSet[/PDF]>>/Subtype/Form/Type/XObject>>stream
0.749023 g
0 0 8 8 re
f
endstream
endobj
8 0 obj
<</BBox[0.0 0.0 8.0 8.0]/FormType 1/Length 43/Matrix[1.0 0.0 0.0 1.0 0.0 0.0]/Resources<</ProcSet[/PDF]>>/Subtype/Form/Type/XObject>>stream
0.749023 g
0 0 8 8 re
f
q
1 1 6 6 re
W
n
Q
endstream
endobj
9 0 obj
<</BBox[0.0 0.0 8.0 8.0]/Filter[/FlateDecode]/FormType 1/Length 82/Matrix[1.0 0.0 0.0 1.0 0.0 0.0]/Resources<</Font<</ZaDb 155 0 R>>/ProcSet[/PDF/Text]>>/Subtype/Form/Type/XObject>>stream
Hâ*‰2T0T0¬¢TÆpÆ<.ß.˝®Dó$S=3Öê4.C=3cC##=CÖê.S=cK#
Ö .c;Öê,.◊Æ@.ÄA~q
endstream
endobj
10 0 obj
<</BBox[0.0 0.0 8.0 8.0]/FormType 1/Length 24/Matrix[1.0 0.0 0.0 1.0 0.0 0.0]/Resources<</ProcSet[/PDF]>>/Subtype/Form/Type/XObject>>stream
0.749023 g
0 0 8 8 re
f
endstream
endobj
11 0 obj
<</BBox[0.0 0.0 8.0 8.0]/FormType 1/Length 43/Matrix[1.0 0.0 0.0 1.0 0.0 0.0]/Resources<</ProcSet[/PDF]>>/Subtype/Form/Type/XObject>>stream
0.749023 g
0 0 8 8 re
f
q
1 1 6 6 re
W
n
Q
endstream
endobj...If you saved these guts to a file named something like 1040f.pdf, then you’d have a PDF containing the IRS 1040 form. Well, not really (since we’ve truncated the file contents), but that’s the idea. So, in essence, all these characters are what makes up a PDF. Delete one of them, and it’s possible you’ll break the whole thing. Click if you want to learn more about PDF structure/syntax.
Conclusion
By understanding the roles of encryption, user passwords, and owner passwords, you can manage how your PDFs are accessed and manipulated by most users. However, it’s crucial to recognize that these security measures are not infallible. Determined users with the right tools can often find ways to bypass restrictions, and simple actions like screen capturing can undermine your efforts to protect sensitive information. If your business is smaller and your product demand small or niche, these concerns shouldn’t stop you. Most of your customers are kind, busy, and won’t see the value in stealing your product.
Setting PDF file permissions using PDF Ink can help control access to your documents. While PDF permissions can help safeguard your documents, they should be part of a broader, multi-layered strategy for information security. By being aware of the limitations and taking proactive steps, you can better protect your valuable content in an increasingly digital world.